7 Ways Someone Can Read Your Text Messages from Another Phone

Have you ever asked yourself, can someone read your text messages from another phone? If the answer is yes, you're not alone and it's not just paranoia.

With so many apps and tech tricks out there, it's easier than ever for someone to peek into your texts without you knowing. This guide breaks down 7 detailed methods people use.
Is It Possible to Read Text Messages from Another Phone
Yes, it's possible to read text messages from another phone. Many think you need physical access to read someone's texts, but that's not true.
From cloud syncs to spyware and message-forwarding features, people have found workarounds that let them spy remotely.
If you're wondering can someone read your text messages from another phone?, here's everything you need to know plus how it's done, why it's done, and how to protect yourself.
Why Would Someone Want to Read Your Texts from Another Phone?
It's not always malicious sometimes it's out of concern. Parents may want to protect kids, partners might fear cheating, or bosses might monitor work devices. But hackers? They do it for your data.
If you've ever wondered someone can read your text messages from another phone or not, think about who might benefit and why.
Signs Someone May Be Reading Your Texts from Another Phone

Wondering can someone read your text messages from another phone? Look for these clues:
- Unusual battery drain or random overheating- This could indicate background surveillance apps running constantly.
- Unexpected spikes in data usage- Many tracking apps use data to upload your messages and phone activity.
- Messages marked as "read" that you never opened- Someone may be viewing your messages remotely.
- Presence of unfamiliar apps or strange browser history- These could be spyware or tools used to mirror your device.
- Apple ID or Google account login alerts- Notifications about new device logins or security changes are major red flags.
- Disabled or missing security settings- Such as turned-off two-factor authentication or unlinked backup passwords.
7 Ways Someone Can Read Your Text Messages from Another Phone
In today's digital world, it's easier than most people think for someone to gain access to your private messages. Here are 7 common ways someone can read your text messages from another phone:
1. SafeMyKid: The Best Way to Read Text Messages from Another Phone

The most reliable and user-friendly way to view someone else's text messages is through SafeMyKid. It's a trusted parental control tool that lets you monitor messages, calls, social media apps, and more from your own phone.
SafeMyKid works silently in the background, allowing you to access SMS, WhatsApp, Messenger, and even deleted messages, all from a private online dashboard.
Why Use SafeMyKid to Read Someone's Text Messages from Another Phone
If you're seriously wondering how someone could read text messages remotely, SafeMyKid stands out as the safest, most powerful option available. It has quickly become a go-to tool for those needing access to another phone's SMS and chat activity discreetly.
Key features for reading text messages from another phone include:
- SMS Monitoring: View full message threads, contact info, and message history (even deleted texts).
- WhatsApp, Messenger & Social Chat Logs: Access conversations across popular messaging apps.
- Contact Logs & Call History: See who's texting and calling, and when.
- Stealth Mode: Operates silently without the target user's knowledge.
- Message Timestamp Tracking: Know exactly when each message was sent or received.
- Keyword Alerts: Get notified when specific words or names are used in texts.
Whether you're a concerned parent or investigating suspicious behavior in a relationship, SafeMyKid offers powerful, real-time monitoring, without compromising safety or privacy.
How to Use SafeMyKid to Read Someone's Text Messages from Another Phone
Gaining access to someone's text messages might sound complex, but with the right tool like SafeMyKid, it's surprisingly simple and discreet. SafeMyKid provides step-by-step access without physical interference once set up.
How to Read Someone's Text Messages from Another Android Phone
Step 1. Create a SafeMyKid Account on The Official Website
Visit SafeMyKid's website and register using your email.

Step 2. Install The SafeMyKid App on The Target's Android Phone
Follow the setup instructions. You'll need physical access to the device to download and install the SafeMyKid app.
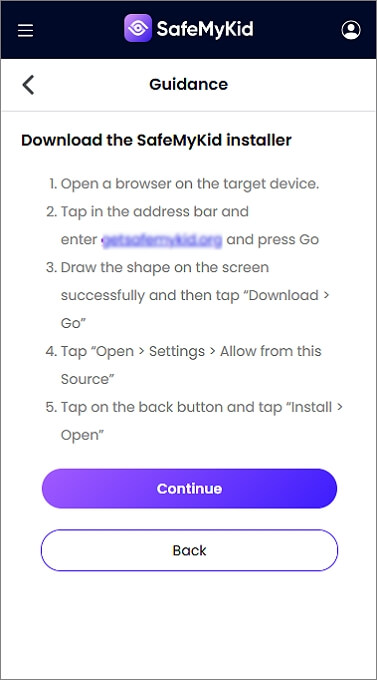
Step 3. Read Someone's Text Messages from Another Android
Log in to your SafeMyKid dashboard from any device. You'll now be able to view text message content, contact names, timestamps, and deleted messages.
How to Read Someone's Text Messages from Another iPhone
Step 1. Sign up
Go to SafeMyKid's website and create your account.

Step 2. Link Your Target's iCloud Credentials
No need to install anything on the iPhone. Just input the iCloud ID and password associated with the device.
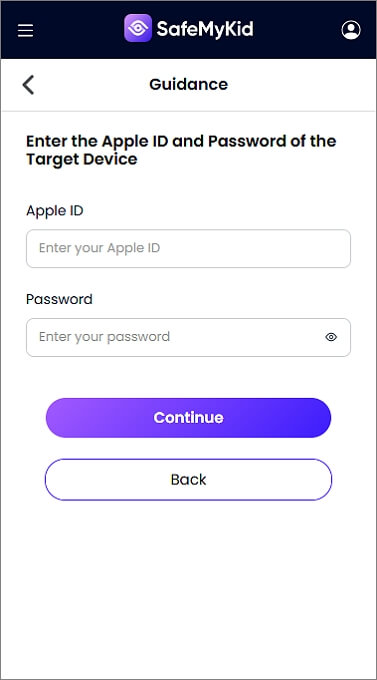
Step 3. Read Someone's Text Messages from Another iPhone
Log into your SafeMyKid control panel to access iMessage content, text history, contact information, and more without ever touching their phones again.

Unlike shady spy apps, SafeMyKid is safe, legal, and transparent. It's perfect for parents, concerned guardians, or anyone needing peace of mind. SafeMyKid remains the most trusted option with superior ease of use and support.
2. iMessage Syncing (Apple Devices)
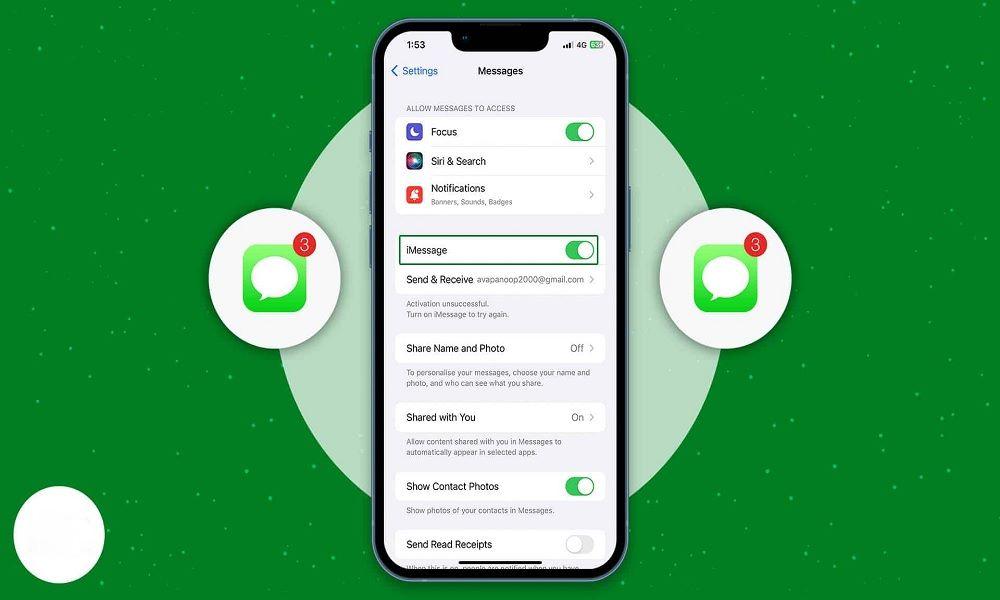
iMessage syncing is one of the easiest and most overlooked ways someone can read your text messages. If your Apple ID is signed in on multiple devices, all messages including pictures and conversations are automatically synced.
This is often used by spouses or family members to keep tabs without needing to touch your iPhone. If you previously logged into your Apple ID on a shared iPad or Mac and forgot to log out, someone could access your entire message history silently.
How it works: Log in to the same Apple ID on another Apple device, activate iMessage, and all synced conversations begin showing up.
Pros:
- Instant access to iMessage across multiple Apple devices.
- No third-party app is required, so it's hard to detect.
Cons:
- Anyone with your Apple ID can exploit this.
- You may not receive a notification that another device is accessing your messages.
3. Google Messages Web or Similar Sync Tools

Google Messages Web allows Android users to send and receive SMS from a computer. This sync is secure, but if someone manages to scan the QR code using your phone, even briefly they could spy on all your messages.
Many users forget to log out, leaving the session active for days. If the person snooping doesn't close the tab, they continue to get live updates of every message you send or receive.
How it works: You open the Google Messages Web portal, scan a QR code with your Android phone, and all messages are mirrored in the browser.
Pros:
- Lightweight and does not require app installation.
- Works in real-time, mirroring the actual chat interface.
Cons:
- QR code can be scanned in seconds if someone gains brief access to your phone.
- You must manually log out, or the session remains active indefinitely.
4. iCloud or Google Account Access (Official Method)

Cloud backups make it possible to retrieve entire text histories without physical access to a phone. If someone has your iCloud or Google credentials, they can download backups to another device or view synced data through the web.
This method is commonly used by partners and tech-savvy individuals. Many don't realize that even deleted messages can be recovered from the cloud if backup is enabled.
How it works: Log in to iCloud or Google Account through a browser or setup wizard. Access messages, app data, and settings synced from the device.
Pros:
- Total remote access, no app needs to be installed on the victim's phone.
- Can recover deleted messages, media, and chat backups.
Cons:
- Requires credentials and, in most cases, two-factor authentication.
- Illegal in many jurisdictions to access someone's cloud without permission.
- Doesn't work if syncing or cloud backup is disabled on the device.
5. SIM Card Cloning

SIM cloning is an advanced method where a duplicate SIM is created to receive all SMS messages meant for the original phone. This technique is often used by hackers or surveillance professionals, and while it's rare, it's very effective.
Cloning can be done using SIM readers, software, and a short access window to your actual SIM. Once cloned, the attacker gets the same messages, including 2FA codes.
How it works: The physical SIM card is copied to another SIM using specific software. Messages sent to the original number are also sent to the clone.
Pros:
- Full access to real-time messages, including OTPs.
- Doesn't require access to cloud services or apps.
Cons:
- Needs physical access and advanced tools.
- Carriers may detect and block multiple SIMs using the same number.
- Illegal and highly traceable if reported.
6. Bluetooth Hacking or Local Exploits

Bluetooth vulnerabilities, though less common today, still pose a risk in crowded areas. An unsecured Bluetooth connection could allow someone nearby to intercept messages or even install spyware.
This method works best when the target device is unpatched, set to "discoverable," and left unattended in public spaces. It's more of a passive threat but still relevant.
How it works: Using specialized tools, attackers connect to your Bluetooth and use exploits to extract data, including text messages or screen content.
Pros:
- No cloud or SIM access is required, just proximity.
- Hard to trace if the attack is brief.
Cons:
- Very limited range (typically 10 meters or less).
- Most modern phones have protections in place.
- Works only when the user has insecure Bluetooth settings.
7. Remote Access Trojans (RATs) or Malware
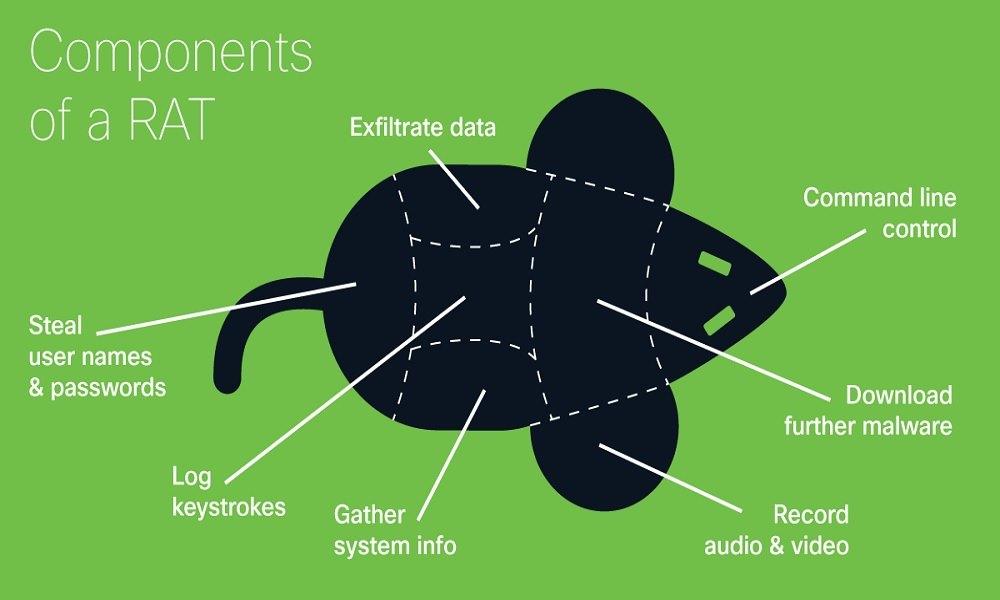
RATs are some of the most dangerous tools used to gain full control over a victim's phone. They are typically hidden in seemingly harmless files or fake apps and can run in the background without alerting the user.
Once installed, they allow attackers to view messages, listen to calls, record screen activity, and even control the device's camera or microphone. This method is used by hackers, stalkers, and cybercriminals.
How it works: A user unknowingly downloads a file (via link, email, or app) embedded with a RAT. Once active, the attacker gets full access to the phone's contents, including messages.
Pros:
- Complete control and real-time monitoring of the target device.
- Can record passwords, screenshots, messages, and more.
Cons:
- Detected by antivirus software if the user is security-aware.
- Highly illegal and a major privacy breach.
How to Protect Yourself from Remote Text Spying
Alt:

The best way to stop others from seeing your messages:
- Use two-factor authentication for iCloud or Google
- Regularly check linked devices
- Avoid public Wi-Fi and don't leave Bluetooth open
- Use anti-spyware tools to scan for hidden apps
- Change passwords regularly, especially if you feel something's off
FAQs on Whether Someone Can Read Your Text Messages from Another Phone
You might want to know more about whether someone can read your text messages from another phone. Here are some of the most common questions people ask along with clear, helpful answers.
1. Can someone read deleted text messages from another phone?
Yes, in some cases, deleted text messages can be recovered and read from another phone, especially if backups exist on iCloud or Google Drive.
Tools like SafeMyKid can access synced backup data (if available) even after messages are deleted from the device. However, once backups are overwritten or deleted, recovery becomes much more difficult.
2. Is it illegal to read someone's text messages without permission?
Yes, in most countries, accessing someone's private messages without their knowledge or consent is considered an invasion of privacy and may violate wiretapping or data protection laws.
Parental monitoring, such as through SafeMyKid, is typically allowed when monitoring minors with legitimate consent or guardianship.
3. Can someone read my messages if they have my phone number?
Having just your phone number is not enough to read your text messages. However, in rare cases, attackers can exploit vulnerabilities (like SIM swapping) to gain access to your phone account and then monitor SMS traffic.
4. How do I know if my iCloud or Google account is compromised?
Signs of a compromised account include unfamiliar login alerts, new devices connected to your account, and strange activity logs. On iCloud, check "Devices" under Settings. On Google, visit your Google Account > Security > Your Devices to see what's signed in.
5. What's the safest way to monitor a child's text messages without invading their privacy?
The safest way is to use transparent parental control tools like SafeMyKid that offer permission-based monitoring. These apps provide clear dashboards, alerts, and control options while allowing parents to respect boundaries and avoid spying without context.
6. Can someone clone my phone and read my texts?
Phone cloning is difficult but possible with access to your SIM card or backups. If someone successfully clones your device, they can receive copies of your text messages. Using eSIMs, setting strong passwords, and keeping physical control of your phone greatly reduces this risk.
7. How long do text message logs stay accessible through third-party apps?
It depends on the app and settings. Most monitoring tools like SafeMyKid keep logs as long as your subscription is active and backups are not deleted. Some apps offer customizable retention settings, allowing you to choose how long to store message history.
8. Can encrypted messaging apps like WhatsApp or Signal be read from another phone?
Generally, no. End-to-end encrypted apps like WhatsApp and Signal are designed so only the sender and recipient can read the messages.
However, if someone installs spyware or gains access to your cloud backups (where messages may be stored), they could potentially retrieve those chats indirectly.
Conclusion
So, can someone read your text messages from another phone? Absolutely, but now you have a solid understanding of how it's done, the tools involved, and most importantly, how to protect yourself.
If you're looking for a reliable and legal way to monitor texts, SafeMyKid is the smartest choice. It's secure, user-friendly, and designed with your family's safety in mind.




