Tips & Tricks: How to Spy on iPhone without Apple ID And Password

If you're researching how to spy on an iPhone without Apple ID and password, you're likely concerned about monitoring a child's device or understanding potential security vulnerabilities to better protect your own device.

This blog explores legitimate monitoring methods, their limitations, and how to protect yourself from unauthorized surveillance.
Understanding iPhone Security and Monitoring Concerns
With over a billion active iPhone users worldwide, understanding security vulnerabilities has become increasingly important.
Apple designs iOS with privacy as a priority, making unauthorized access difficult by design.
Understanding why people seek iPhone monitoring solutions helps highlight both legitimate needs and important security concerns:
- Parental Monitoring: Parents want to ensure children's safety online
- Lost Device Recovery: Locating misplaced or stolen devices
- Business Device Management: Companies managing company-owned devices
- Security Research: Understanding vulnerabilities to improve protection
- Self-Protection Awareness: Learning about risks to better secure personal devices
For those researching iPhone monitoring for legitimate purposes, these considerations emphasize why understanding both capabilities and limitations is crucial.
Is It Possible to Monitor an iPhone without an Apple ID and Password?
The short answer: Yes, but only in very limited ways —— and usually with significant restrictions.
Apple's ecosystem is designed to be private and secure. Features like iCloud, Find My iPhone, and end-to-end encryption all rely heavily on the Apple ID and password to keep user data safe. This makes it nearly impossible to monitor an iPhone remotely and fully without credentials —— unless you have:
- Physical access to the device
- Consent and setup access (e.g., via Family Sharing or MDM)
- Or you're using network-level that still don't reveal everything
Most tools that claim to offer "full remote spying without Apple ID" are either scams, illegal, or require jailbreaking.
How to Monitor an iPhone without an Apple ID and Password: 3 Ways and Their Limitations

Whether you're implementing monitoring for legitimate purposes or protecting against unauthorized surveillance, knowledge of techniques and vulnerabilities is your strongest tool for maintaining digital security and privacy.
1. Network-Based Monitoring
Some monitoring can be accomplished through the network the iPhone connects to rather than the device itself.
How Network Monitoring Works:
- Monitors data traveling through a shared Wi-Fi network
- Can intercept unencrypted communications when on the same network
- May require setting up specialized network equipment
- Captures data in transit rather than stored on the device
- Limited to monitoring when the device uses the specific network
Pros:
- Doesn't require direct access to the target device
- Can monitor multiple devices on the same network
- Doesn't alter the target device's configuration
Cons:
- Limited to shared network environments
- Cannot access encrypted communications (increasingly common)
2. Physical Access Methods

With physical access to an unlocked iPhone, various monitoring solutions can be implemented without needing Apple ID credentials.
How Physical Access Monitoring Works:
- Requires temporary unrestricted access to the unlocked device
- Monitoring software or configuration changes are made directly
- May involve enabling hidden features or installing applications
- Often requires disabling certain security features
- Usually needs only one-time access rather than continuous access
Pros:
- Bypasses many remote authentication requirements
- Can establish persistent monitoring with one-time access
- Allows for precise configuration of monitoring parameters
Cons:
- Requires gaining physical access to an unlocked device
- Time-limited opportunity to complete setup process
3. Specialized Monitoring Software
Various third-party monitoring solutions claim to provide access without Apple credentials, though their effectiveness and legality vary significantly.
How Monitoring Software Works:
- Applications must typically be installed directly on the target device
- They require initial jailbreaking or installation permissions
- Once installed, they may operate in stealth mode
- Data is typically sent to a web dashboard for remote viewing
- Most require at least brief physical access to the device
Pros:
- Can provide more extensive monitoring capabilities
- Some operate in hidden mode without visible indicators
- Offer centralized dashboards for data review
Cons:
- Most legitimate solutions require initial device access
- May violate terms of service or local laws if used without consent
SafeMyKid: The Best Legitimate Monitoring Solution for iPhone

For those seeking a comprehensive and legitimate monitoring solution, SafeMyKid offers powerful tools specifically designed for parental control and device security.
It enables parents to monitor Instagram activity, track screen time, and set usage limits without invading the child's privacy.
SafeMyKid is built to support responsible parenting by offering a balanced approach that ensures both safety and trust.
The platform provides real-time insights and alerts, making it easier for parents to stay informed about their child's online behavior.
With user-friendly features and a strong commitment to data protection, SafeMyKid is a reliable choice for modern digital parenting.
Key Features of SafeMyKid to Spy on iPhone
- Streamlined Setup Process: Simple installation with clear parent/guardian controls
- Activity Monitoring: Track app usage, screen time, and digital habits
- Location Tracking: Real-time location services with history and geofencing
- Content Filtering: Block inappropriate content and applications
- Communication Oversight: Monitor messaging and social media activity
- Transparent Operation: Ethical approach with appropriate disclosure
- Regular Reports: Detailed insights into digital behavior patterns
How to Set up SafeMyKid to Spy on iPhone in Real Time
Setting up SafeMyKid provides immediate monitoring capabilities while maintaining ethical standards.
Step 1. Sign up and Create an Account
Register with your email address and create a secure password. Follow the on-screen instructions to complete your account setup.

Step 2. Set up The SafeMyKid App
Simply log in using the iCloud credentials associated with the device. No physical installation is required.
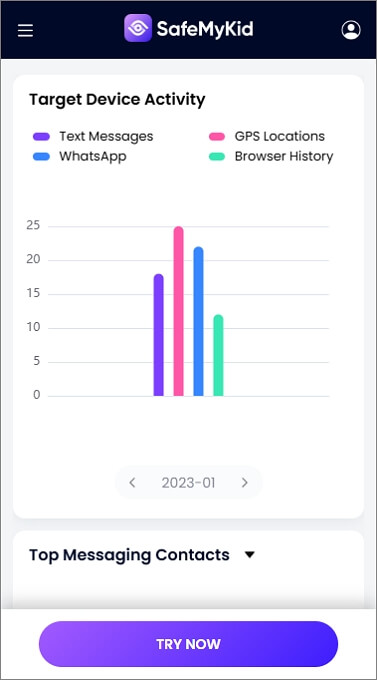
Step 3. Use SafeMyKid to Spy on iPhone in Real Time
Log in to your SafeMyKid dashboard to view monitored activities, location data, and receive alerts about potential issues or concerns.
Why Would Someone Want to Monitor an iPhone without an Apple ID and Password?
Let's be honest —— there are many reasons why someone might want to monitor an iPhone without having full access to the Apple ID. Not all of them are shady. Some are actually quite reasonable:
1. Parental Control
Parents often want to protect their kids from online dangers —— from cyberbullying to inappropriate content. But tech-savvy teens may refuse to share their Apple ID or change passwords often. Monitoring tools can help ensure their safety without constant confrontation.
2. Lost or Stolen Device
If you're trying to locate your own lost iPhone or a family member's, and don't have the Apple ID/password handy, alternative monitoring methods might help, like GPS or network tracking.
3. Business Device Monitoring
Companies that issue work phones want to ensure employees are using devices responsibly. With tools like MDM, they can monitor usage without needing personal Apple ID credentials, especially if the phone is company-owned.
4. Relationship Concerns
Some individuals may turn to phone monitoring due to suspicions of cheating or dishonesty in a relationship. While this is a common motivation, it's also a legal and ethical grey area —— and may violate privacy laws.
5. Elderly or Vulnerable Family Members
Monitoring tools can help keep track of elderly loved ones or individuals with cognitive challenges who might wander off, fall victim to scams, or get lost. In such cases, access to their iPhone location and activity can offer peace of mind.
How to Protect Your iPhone from Unauthorized Monitoring
Understanding monitoring methods is also valuable for protecting your own device from unwanted surveillance:
- Keep iOS Updated: Install security patches as soon as available
- Use Strong Passcodes: Create complex alphanumeric passcodes
- Enable Two-Factor Authentication: Add an extra layer of security to your Apple ID
- Review App Permissions: Check which apps have access to location, camera, etc.
- Check Profiles & Certificates: Remove any suspicious profiles in Settings
- Audit Connected Devices: Review which devices are signed into your Apple ID
- Be Cautious with Physical Access: Don't leave your unlocked phone unattended
- Check for Jailbreaking: Restore to factory settings if you suspect unauthorized modifications
- Monitor Battery Performance: Unusual drain may indicate background monitoring
- Review Network Connections: Use trusted networks and consider a VPN
FAQs about iPhone Monitoring without Apple ID
Now that you understand monitoring capabilities and limitations, you might have additional questions about iPhone monitoring.
1. Is it legal to monitor an iPhone without the user's knowledge?
Generally legal only when monitoring your minor child's device or company-owned devices with proper disclosure; monitoring another adult's device without consent is illegal.
2. Can someone monitor my iPhone without me knowing?
While difficult, risk factors include giving someone physical access to your unlocked device, installing profiles from untrusted sources, jailbreaking your device, or connecting to compromised networks that could enable unauthorized surveillance.
3. How can I tell if my iPhone is being monitored?
Watch for unusual battery drain, unexpected performance issues, strange background noise during calls, abnormal data usage patterns, and unfamiliar apps.
4. Do monitoring solutions work on all iPhone models and iOS versions?
Most legitimate solutions work on current iPhones, but capabilities vary significantly; newer iOS versions implement stronger security features that limit monitoring options.
5. Are there any completely remote monitoring methods that require no device access?
Despite marketing claims, virtually all effective monitoring solutions require at least initial access to either the device or associated accounts; solutions claiming "100% remote access" are typically misleading or ineffective.
Conclusion
Understanding how to spy on an iPhone without an Apple ID and password is valuable both for legitimate monitoring needs and for protecting your own device security.
By recognizing the methods, limitations, and legal considerations involved, you can make informed decisions about monitoring.




