How to Log into Someone's Instagram without Them Being Notified-the Ultimate Guide in 2025

How to log into someone's Instagram without them being notified raises ethical and security concerns, as Instagram's alerts, 2FA, and device recognition prevent unauthorized access.
In 2025, Instagram's advanced algorithms detect suspicious activities, making unnoticed access nearly impossible. Enabling 2FA, monitoring login devices, and avoiding scams are essential for secure and ethical social media use.
Important Security Features to Know before Trying to Log into Someone's Instagram without Them Being Notified
If someone tries to log into an Instagram account without the owner being notified, they must understand the security features designed to prevent unauthorized access. These features actively protect users and make it challenging to bypass detection:
- Real-Time Login Notifications : Instagram immediately alerts users via push notifications and email when a login attempt is made from a new device or an unfamiliar location.
- IP Address Tracking : Instagram tracks the IP address during login attempts and flags suspicious locations that differ from the usual login patterns.
- Two-factor authentication (2FA) : This adds a second security step, requiring a unique code sent to the user's phone or email, making unauthorized access more difficult.
- Login Verification Prompts : Instagram may prompt a security question or ask for confirmation from the user's verified device to confirm a login.
- Login History and Device Tracking : The app provides access to a detailed history of login activities, including date, time, and device information, making any unauthorized logins traceable.
- AI-Based Suspicious Activity Detection : Instagram's algorithms monitor login behavior to identify unusual activity, such as multiple failed password attempts or logins from distant geographic locations.
- Browser and App-Based Session Protection : Even if someone gains the password, Instagram might automatically log out users from old sessions and send a session-expiration notification.
These advanced security mechanisms significantly reduce the chances of logging into someone's Instagram without triggering an alert, reinforcing user privacy and safety.
The Best Way to Log into Someone's Instagram without Them Being Notified Using SafeMyKid

SafeMyKid allows parents to monitor Instagram activity directly on the target device, avoiding server access that triggers login alerts. It provides undetectable access to messages, posts, and history without needing the account password.
SafeMyKid needs physical access to the child's device for installation and setup. Once configured, it runs discreetly, collecting Instagram activity without triggering security alerts.
SafeMyKid provides stealth monitoring but should be used ethically and legally. Parents must inform children to maintain trust and comply with privacy laws. It is intended for child safety, not unauthorized access.
Key Features of SafeMyKid - Instagram Spying App
If someone attempts to discreetly monitor Instagram without triggering alerts, certain app features may help avoid detection. Below are key functionalities often used for silent Instagram tracking:
- Invisible Mode : Operates completely hidden on the target phone, ensuring the user remains unaware.
- Stealth Instagram Monitoring : Tracks Instagram activity, including messages, posts, and interactions, without needing the account password.
- Bypassing Login Notifications : This avoids login alerts by monitoring Instagram directly from the device, not through Instagram servers.
- Real-Time Tracking : Provides live updates of Instagram usage and login sessions while avoiding detection.
- Discreet App Operation : Runs in stealth mode, preventing the account owner from noticing any monitoring activity.
- Session Tracking Without Alerts : Tracks ongoing Instagram sessions without triggering suspicious activity alerts.
- Device-Based Monitoring : Accesses Instagram data directly from the target device, bypassing server-side security.
- Hidden Location Tracking : Detects Instagram usage locations without sending login alerts to the user.
- App Usage Tracking : Monitors Instagram screen time, app usage, and browsing without alerting the user.
How to Set up SafeMyKid to Log in to Instagram Accounts without Them Being Notified
Setting up SafeMyKid for discreet Instagram monitoring requires careful configuration to avoid triggering login alerts.
Step 1. Register and Establish an Account
Register by going to the SafeMyKid website.

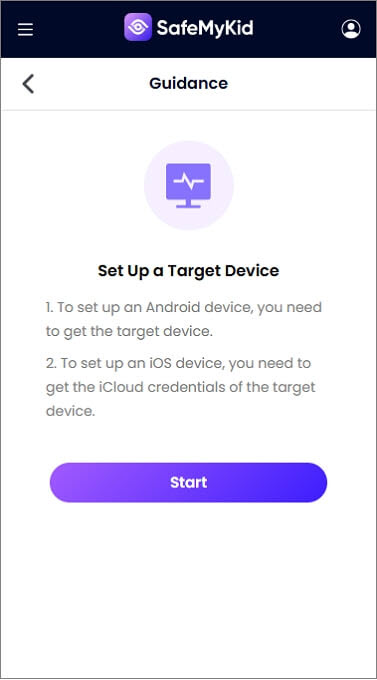
Step 2. Configure The Target Device for SafeMyKid
- For iPhones: Use iCloud to log in; no software is necessary.
- Install the SafeMyKid app on your Android device and turn on stealth mode.
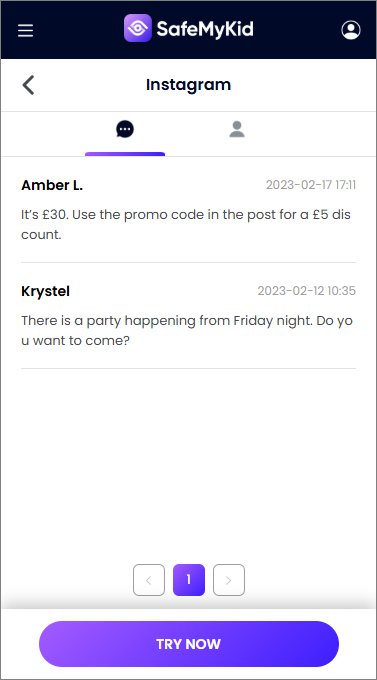
Step 3. Logging into Someone's Instagram Account without Them Being Notified
Access Instagram activity discreetly through the SafeMyKid dashboard without logging in directly.
5 Ways People Attempt to Log into Someone's Instagram without Being Notified

Before attempting to access someone's Instagram, people often try to bypass security measures undetected. However, Instagram has strong protections in place to prevent unauthorized logins. Here are some common methods people attempt, though many are risky and unethical.
1. Using Saved Passwords on Shared Devices
If someone has previously logged into their Instagram account on a shared or public device and opted to save their login credentials, others with access to that device might open the app or website and gain entry without needing the password. This method relies on the target's oversight in managing saved passwords and device access.
Limitations:
- Requires physical access to a device with saved credentials
- Many users consistently log out of shared devices
- Two-factor authentication prevents access with just a password
- Instagram's automatic logout feature on public devices
2. Resetting Password via Email or Phone Number
One of the more common methods involves initiating a password reset through Instagram using the person's linked email address or phone number. If the attacker has access to either, they may be able to change the password and log in. However, Instagram typically notifies the account owner via email or SMS, making this method risky and easily detected.
Limitations:
- Requires access to the target's email or phone
- Instagram sends immediate notifications about password changes
- Two-factor authentication prevents simple resets
- Unusual login activity triggers additional security measures
3. Session Hijacking
This advanced method involves intercepting an active Instagram session, usually over unsecured or public Wi-Fi networks. Tools like packet sniffers are used to steal session cookies. However, Instagram has robust security protocols that often detect unusual activity and force a logout or request re-authentication, making this method challenging and unreliable.
Limitations:
- Instagram uses HTTPS encryption, making interception difficult
- Requires advanced technical knowledge
- Instagram monitors for unusual access patterns
- Session tokens expire quickly, limiting opportunity
4. Using Keyloggers
Keylogging software records every keystroke made on a device, capturing login information when the target types their Instagram username and password. This method requires the attacker to either physically access the device or install the software remotely——both of which can be difficult to achieve without detection or the right level of access.
Limitations:
- Requires installation access to target's device
- Modern security software detects most keyloggers
- On-screen keyboards can bypass traditional keyloggers
- Two-factor authentication provides protection even if the password is captured
5. Accessing Browser Autofill Data
Modern browsers offer to save and autofill login credentials for convenience. If someone gains access to a target's device, they might retrieve saved Instagram login details from the browser's password manager. Some browsers require a master password or device authentication, but if not set up, it becomes a potential vulnerability.
Limitations:
- Modern browsers encrypt saved password data
- Often requires system-level authentication to access
- Requires physical access to an unlocked device
- Many users opt not to save social media passwords
Are Methods to Log into Someone's Instagram Safe and Legal?
Accessing someone's Instagram without permission is illegal in most countries and can lead to fines or imprisonment. It also raises serious ethical and legal concerns under cybercrime and privacy laws.
Additionally, the safety of these methods is questionable. Many techniques, like keylogging, or password cracking, are not only illegal but also risky, as they expose users to malware, data breaches, and tracking.
Instagram's security features, such as two-factor authentication (2FA), login alerts, and device recognition, make it difficult to gain access undetected.
Ultimately, violating someone's privacy by accessing their Instagram account without permission is unsafe, illegal, and unethical.
How Instagram Detects Unauthorized Logins
Instagram detects unauthorized logins through advanced security features designed to protect user accounts. One key mechanism is login alerts, which notify users whenever their account is accessed from a new device or location.
These alerts are triggered when Instagram identifies unusual login behavior, such as access from a different country, an unfamiliar device, or an unusual IP address.
Another layer of protection is device recognition, where Instagram remembers previously used devices. If someone tries logging in from an unrecognized device, Instagram may ask for additional verification, such as entering a code sent via email or SMS.
Why Understanding Instagram's Security Features Is Critical in 2025
In 2025, Instagram significantly advanced its security measures, making it increasingly difficult for anyone trying to figure out how to log into someone's Instagram without them being notified. Features like real-time login alerts, device tracking, and AI-based suspicious activity detection are designed to instantly flag unauthorized access attempts.
Tools such as two-factor authentication (2FA), and instant login notifications ensure that account owners are immediately informed of any login activity——making stealthy access nearly impossible. These safeguards not only deter unauthorized access but also empower users to respond quickly to potential threats.
Understanding these security features is vital——not for bypassing them——but for appreciating how far digital platforms have come in protecting user privacy. Staying informed allows users to take control of their security and reinforces the importance of ethical online behavior.
FAQs about Logging into Someone's Instagram without Being Notified
When it comes to logging into someone's Instagram without being notified, users often have questions about security, legality, and available tools. Here are some frequently asked questions:
1. Does Instagram detect logins from unrecognized devices?
Yes, Instagram uses device recognition to flag unfamiliar login attempts and alert users.
2. Can monitoring apps like SafeMyKid be used for Instagram access?
SafeMyKid can monitor Instagram activity on a child's device, but it should be used ethically and legally.
3. What is two-factor authentication (2FA), and how does it affect logins?
2FA adds an extra security layer by requiring a code sent to the user's phone or email.
4. Is it possible to avoid Instagram's suspicious activity detection?
Instagram's AI actively detects unusual login patterns, making stealthy access difficult.
5. Do login notifications get sent when accessing Instagram from a new browser?
Yes, Instagram sends email or in-app alerts for logins from unfamiliar browsers.
Conclusion
Bypassing security to learn how to log into someone's Instagram without them being notified is illegal. Features like 2FA and login alerts prevent unauthorized access, ensuring privacy.
Accessing someone's Instagram without consent can result in legal consequences under cybercrime laws. Respecting privacy and practicing ethical online behavior are essential for navigating the digital world responsibly.



