Hack Text Messages without Access to a Phone: 5 Proven Ways

Ever wondered if it's really possible to hack text messages without access to a phone? The truth is——it is. And there are several ways to go about it.

In this guide, you'll learn how to hack text messages without access to phone legally, when it's okay to do so, and the six best methods that actually work.
Is It Really Possible to Hack Text Messages without a Phone?
Yes——it's totally possible to hack text messages without access to phone using specific apps and techniques. But don't get ahead of yourself. Whether it's legal or not depends on the reason you're doing it.
If you're a parent trying to keep your kids safe online or an employer managing company devices, monitoring messages can be justified. But accessing someone's texts without their permission? That's a privacy violation and possibly illegal.
So, before diving into the methods, let's talk about the top legal and safe way to do it——especially for parents.
5 Powerful Ways to Hack Text Messages without Access to a Phone
There are several methods that claim to let you read someone's text messages without having physical access to their phone. Here are 5 of the most reliable approaches:
1. SafeMyKid: The Best Way to Hack Text Messages without Access to a Phone

When it comes to smart monitoring, SafeMyKid is hands down the top pick. It's not just a spy tool——it's a full parental control and phone monitoring platform designed to help parents keep their kids safe in the digital world.
What makes SafeMyKid stand out is its ability to work seamlessly without needing physical access to the target phone, especially for iPhones. With just the iCloud credentials, parents can start monitoring SMS, iMessages, app activity, and more.
Why Choose SafeMyKid to Hack Text Messages without Access to a Phone?
SafeMyKid stands out for its reliability and ease of use when monitoring text messages without accessing the target phone. Unlike many other apps, it offers a seamless solution for both Android and iPhone devices. Here are some key reasons to choose it:
- View incoming and outgoing text messages: Get detailed insights into text conversations, including deleted messages.
- Real-time alerts and activity tracking: Receive immediate updates on new messages and activities, keeping you informed at all times.
- Operates in stealth mode: SafeMyKid runs invisibly, so the target user won't know it's being monitored.
- Works on Android and iPhone: Whether it's an Android or iOS device, SafeMyKid is compatible with both.
- Easy to set up and user-friendly dashboard: No technical expertise is required to start tracking——simply install and begin monitoring.
Whether you're dealing with hacked text messages without access to the phone's Android or iPhone, SafeMyKid makes it hassle-free and secure.
How to Use SafeMyKid to Hack Text Messages without Access to The Phone
If you're looking for a safe, reliable way to monitor text messages without accessing the phone, SafeMyKid provides an easy solution.
How to Hack Text Messages without Access to an Android Phone
Step 1. Register on SafeMyKid
Create an account on the SafeMyKid website using your email address.

Step 2. Install The App on The Target Android
Follow the easy installation steps provided by SafeMyKid to set up the app on the target Android phone.
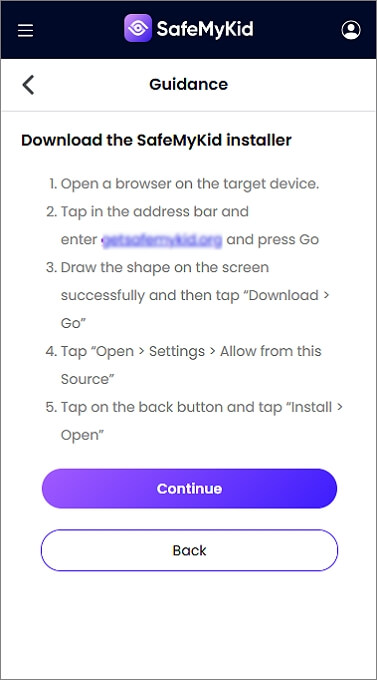
Step 3. Start Hacking Text Messages without Access to an Android Phone
Log in to your SafeMyKid dashboard to monitor incoming and outgoing text messages in real time.
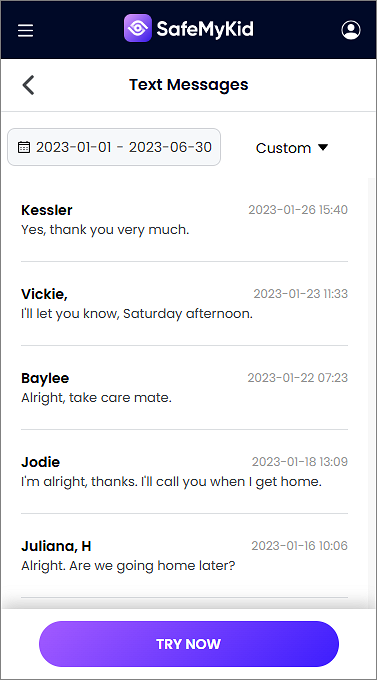
How to Hack Text Messages without Access to an iPhone
Step 1. Sign up for a SafeMyKid Account
Create an account using your email address only.

Step 2. Enter The iCloud Credentials of The Target iPhone
For iPhone, you don't need to install any software; simply enter the iCloud login credentials of the target phone.
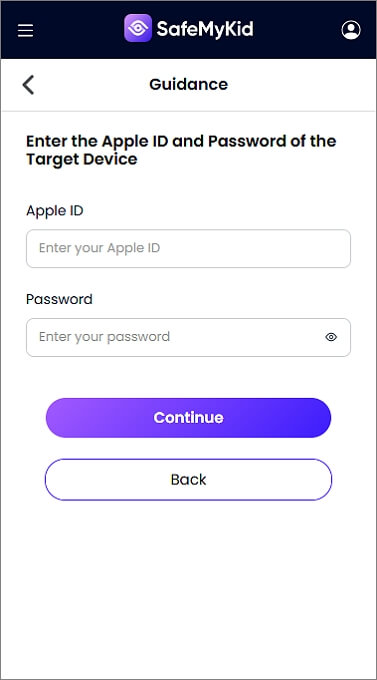
Step 3. Hack Text Messages without Access to iPhone
You can begin tracking messages and other activities remotely via the SafeMyKid dashboard.

SafeMyKid offers the most seamless way to hack text messages without access to the phone for free (trial available) with full control and legal use.
2. iCloud Sync (Official Method for iPhones)
If the person you want to monitor is using an iPhone, and you know their Apple ID and password, you're in luck. iCloud automatically backs up messages, which can be accessed remotely.
How It Works:
- Log in totheir iCloud account
- Navigate to messages or use a linked app to view backups
- Sync messages to another iOS device
Advantages:
- No need to touch the phone
- 100% legal if you have permission
- Works well if iCloud backup is enabled
Disadvantages:
- Doesn't work if two-factor authentication (2FA) is enabled
- Access can be revoked by changing the Apple ID password
- No real-time message tracking
3. Google Account Sync (Official Method for Android)
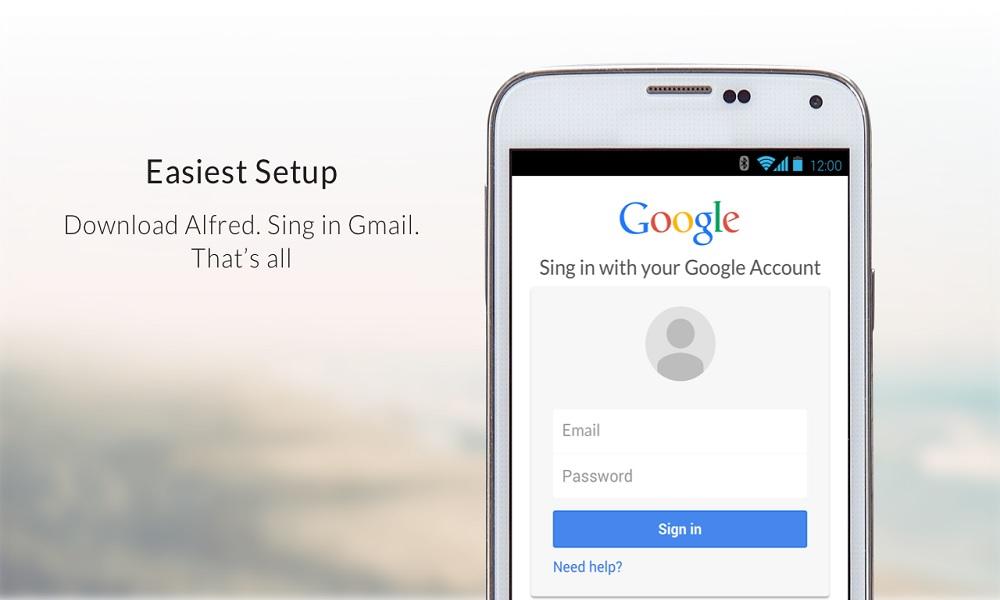
On Android, users can back up SMS messages to their Google account. If you have the login credentials, you may be able to retrieve messages from Google Drive.
Steps:
- Log in totheir Google account
- Check Google Drive backups
- Use a data recovery tool ora linked service
Advantages:
- Official and doesn't require installation
- Can be used for free
Disadvantages:
- No access to live messages
- Requires backup to be enabled beforehand
- May not include third-party chat messages (e.g., WhatsApp)
4. Message Mirroring Apps (Partial Access)

Apps like Pushbullet or AirDroid can mirror text messages from the target phone to another device. These apps typically require setup on the target phone first.
How It Works:
- Install the app on the target device
- Link it to your device or web account
- Receive mirrored SMS messages
Advantages:
- Allows remote monitoring of text messages.
- Easy setup and user-friendly interface.
- Works across different platforms, including Android and Windows.
Disadvantages:
- Requires physical access at least once
- Notifications may reveal the connection
- Doesn't work well for iPhones
5. SIM Cloning or SIM Swap (Advanced Method)

This is a more technical and risky approach. SIM cloning means copying the SIM card to intercept messages. It's a tactic used by hackers to bypass 2FA codes or intercept messages.
How It Works:
- Clone the SIM using specific software and hardware
- Insert the clone into a device
- Receive all SMS meant for the target
Advantages:
- Allows access to all incoming and outgoing SMS messages.
- Effective for intercepting 2FA codes, which can be used for account access.
- Offers complete control over the phone's SMS communication.
Disadvantages:
- Highly illegal and unethical, violating privacy laws in most countries.
- Requires technical expertise and expensive equipment.
- Risk of getting caught, as it's a crime in many jurisdictions.
- Vulnerable to detection, as the original SIM may be deactivated once a clone is made.
When Is It Legal to Hack Someone's Texts?

It's legal to hack text messages in the following scenarios:
- Parent monitoring a minor: Parents have the right to monitor their child's communication to ensure their safety.
- Device owner monitoring their own property: If you own a company phone, you are allowed to monitor the device.
- Full consent from the person being monitored: If someone willingly agrees to allow you to monitor their messages, it is legal.
However, it's illegal and unethical to hack text messages without access to the phone for spying on partners, friends, or random users without permission. You could face legal consequences.
Risks of Hacking Text Messages without Access
Trying to hack text messages without access to a phone comes with serious risks that can lead to serious consequences. These include:
- Legal Penalties: Unauthorized access to someone's messages violates privacy laws, which can result in fines, criminal charges, or civil suits.
- Malware Risks: Many free "hacking" apps are actually scams designed to steal personal information or infect devices with malware.
- Exposure of Personal Data: Using untrustworthy methods to hack text messages may expose your own sensitive data to hackers.
- Ruined Relationships: Engaging in unauthorized monitoring can cause irreparable damage to relationships, leading to mistrust, emotional harm, or even legal disputes.
Be wary of hack text messages without access to phone-free tools——most of them are scams or malware traps.
FAQs on Hack Text Messages without Access to Phone
Still have questions about how to hack text messages without access to a phone safely and effectively? Below, we've answered some of the most common queries to help you better understand your options and stay informed.
1. Can I hack text messages without access to an Android phone using a third-party app?
Yes, it's possible to hack text messages without access to an Android phone using trusted third-party apps. These apps typically require a one-time setup on the target device, after which they run silently in the background.
SafeMyKid is one of the most effective tools for this purpose due to its ease of use and stealth operation. Always make sure to use such apps within the bounds of the law, such as for parental control or employee monitoring.
2. Is there a completely free tool to hack text messages without access to a phone?
Most tools claiming to hack text messages without access to phone free are scams or may contain malware.
Legitimate monitoring apps like SafeMyKid may offer limited free trials, but full features usually require a subscription. Be cautious of websites or apps that promise full-text access for free——they're rarely secure or legal.
3. How effective is a hack on text messages without access to the phone app on iPhones?
Hacked text messages without access to the phone app for iPhones typically don't work the same way as it does on Android due to Apple's strict privacy rules. Most iPhone monitoring relies on iCloud backup and credentials.
Apps like SafeMyKid bypass the need for physical access by using the user's iCloud account (with permission), making them ideal for monitoring iPhones legally and effectively.
4. Can you hack text messages without access to the phone for free using online services?
Some websites claim you can hack text messages without access to the phone for free, just by entering a number, but these are almost always fake. Real monitoring solutions require either installation or login credentials. Instead of risking your personal data on shady services, use a trusted platform like SafeMyKid, which offers secure and transparent access with trial options.
5. Are there different methods for Android and iPhone when hacking messages?
Yes. For Android, most tools require a lightweight app to be installed on the target device to hack text messages without access to the phone. For iPhones, installation is usually not needed if iCloud credentials are available. SafeMyKid supports both platforms with tailored processes, making it versatile for cross-device tracking.
6. What permissions are needed to use SafeMyKid on an Android device?
To use SafeMyKid to hack text messages without access to Android phone, you'll need to enable permissions like SMS access, location services, and device administration. These permissions are essential for the app to function properly in the background.
7. Is it legal to use hacked text messages without access to the phone app on a spouse's device?
Monitoring a spouse's device without their consent is not legal in most regions, even with a hacked text message without access to the phone app. While suspicions may arise in relationships, it's important to seek legal or counseling support rather than violate someone's privacy.
8. How long does it take to start monitoring after setup is complete?
Once SafeMyKid is installed and synced, monitoring usually begins within minutes. To hack text messages without access to an iPhone, syncing with iCloud is immediate if credentials are valid and backup is enabled.
Android users can start seeing messages and activities as soon as the app finishes setup and permissions are granted.
Conclusion
Yes, you can hack text messages without access to the phone, but only under legal and ethical circumstances. The best and safest way? Use SafeMyKid, especially for keeping your children safe.
If you're using official methods like iCloud or Google backup, make sure you understand both the benefits and the limits. And whatever you do, stay within the law.




