How to Access Someone's Phone without Them Knowing: 6 Effective Tips

Sometimes you need to know what's going on with someone's phone, maybe for your child's safety or to check on a loved one. The good news? It's possible.
This guide walks you through 6 effective ways on how to access someone's phone without them knowing. But before we dive into the tech side, let's cover what's okay and what's not.

When Is It Okay to Access Someone's Phone without Them Knowing?
There are a few scenarios where it's considered ethical and sometimes even necessary to monitor someone's phone:
- Parental Monitoring: Parents may monitor their child's phone to protect them from online risks and ensure their safety.
- Work Devices: Employers can oversee company-owned phones to ensure proper use and protect sensitive information, often with employee consent.
- Lost or Stolen Phones: Tracking your own lost or stolen device to recover it is justified.
If you fall into one of these categories, you're probably in the clear.
Now let's get into how to access someone's phone without them knowing, starting with the most effective solution.
3 Proven Methods to Access Someone's Phone without Them Knowing
Accessing someone's phone without their knowledge raises important privacy and ethical questions. However, there are legitimate situations where discreet access is necessary, such as parental control or device recovery.
Below are three proven methods commonly used for this purpose.
1. Use SafeMyKid (The Best for Android and iPhone Monitoring)

If you're looking for a smart, stealthy, and legal way to monitor a phone, SafeMyKid is the go-to solution. SafeMyKid offers a reliable way to monitor Android and iPhone devices without alerting the user.
Designed primarily for parents and guardians, it runs discreetly in the background, tracking app usage, messages, social media activity, and even location in real time. It doesn't require rooting or jailbreaking the device, making setup easier and safer.
Why Use SafeMyKid to Access Someone's Phone without Them Knowing
SafeMyKid is a trusted monitoring app designed specifically for parents who want to ensure their children's safety discreetly. It works seamlessly on both Android and iPhone devices, running quietly in the background without triggering any alerts. The app provides comprehensive access to essential phone data, including:
- Real-Time GPS Tracking: Instantly track your target's live location and receive updates with detailed route history. You can also set up geofencing alerts to be notified when your target enters or leaves specific areas (like home, school, or a friend's house).
- Social Media Monitoring: Monitor activities on popular platforms such as WhatsApp, Instagram, Snapchat, Facebook, and Telegram. See messages, photos, videos, last seen, and interactions to stay informed about who your target is communicating with.
- Call Logs and SMS Access: Review all incoming, outgoing, and missed calls along with timestamps and contact details. You can also read SMS conversations, even those that have been deleted.
- Browser History Tracking: Gain insight into your target's browsing habits, including visited websites, search terms, and online behavior patterns.
- Multimedia Access: View all photos, videos, and audio files stored or received on the device. This helps detect inappropriate or unsafe content early.
- Stealth Mode Operation: The app remains invisible on the device and doesn't consume noticeable battery or system resources, ensuring it doesn't raise suspicion.
- Web & App Blocking: Restrict access to inappropriate websites or applications by blocking them remotely, ensuring a safer browsing experience.
All of this is accessible remotely via a secure dashboard, making it easy to monitor without physical access to the phone after setup.
How to Use SafeMyKid to Access Someone's Phone without Them Knowing
If you want a reliable way to monitor a phone discreetly, SafeMyKid offers simple setup options tailored for both Android and iPhone devices. Below is a step-by-step guide to help you get started quickly and maintain covert access.
How to Access Someone's Android Phone without Them Knowing
Step 1. Sign up
Create your SafeMyKid account on their website.

Step 2. Install The SafeMyKid App
You'll need brief physical access to the target Android phone to download and install SafeMyKid.
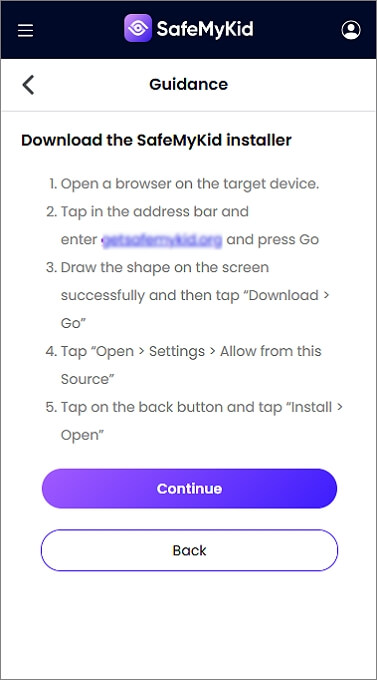
Step 3. Access Someone's Android Phone without Them Knowing
Once installed, log into your SafeMyKid dashboard from any device to monitor activity discreetly in real time.
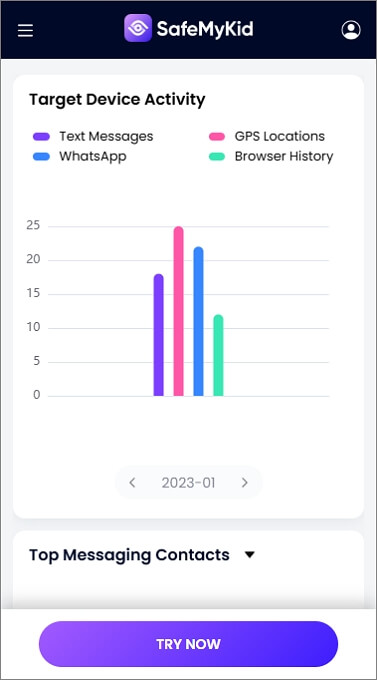
How to Access Someone's iPhone without Them Knowing
Step 1. Sign up
Set up your SafeMyKid account online.

Step 2. Input iCloud Details
No installation is required. Simply enter the target device's iCloud credentials to sync data remotely.
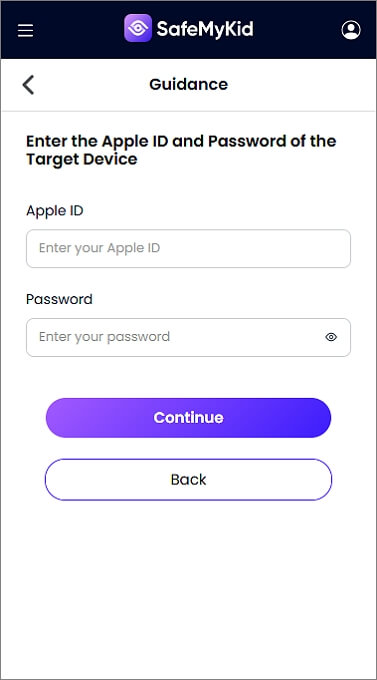
Step 3. Access Someone's iPhone without Them Knowing
Access the dashboard anytime to view messages, location, social activity, and more.

If you want peace of mind, SafeMyKid is the safest and most effective tool available today.
2. iCloud Monitoring (iPhone Only)

With access to someone's iCloud credentials, you can log into iCloud.com to view iMessages, photos, notes, and some app activity remotely. This method doesn't require a physical device, making it convenient.
However, it won't give access to third-party apps like WhatsApp, and logging in may trigger security notifications on the target device, potentially alerting the user.
Pros:
- No physical access is needed; fully remote
- Access to iMessages, photos, and notes
Cons:
- Does not cover third-party apps like WhatsApp or Instagram
- Login alerts may notify the target user
3. SIM Swap or Call Forwarding

SIM swapping or call forwarding reroutes calls and texts from the target's phone to your device, allowing you to intercept communications. This method involves cloning the SIM card or setting up call forwarding remotely.
It is highly risky, often illegal, and typically detectable by the user. It also does not provide full access to the phone's data, only SMS and calls.
Pros:
- Can intercept calls and text messages
- Sometimes used by law enforcement or investigators
Cons:
- Illegal in many jurisdictions
- The risk of detection is high
- Does not provide access to apps or other phone data
3 Easy Ways to Access Someone's Phone with Their Awareness or Consent
There are situations where accessing someone's phone with their awareness or consent becomes necessary. Below are 3 easy and responsible methods to do so without breaching trust or privacy laws.
1. Remote Access Tools Like Splashtop

Splashtop is primarily an IT remote support tool, but it can also be used to mirror and control Android devices from another location. After installing the app on both the target and your device, you can view the phone's screen in real time and control apps remotely.
This can be helpful for troubleshooting or monitoring purposes, but it requires the target phone to remain connected to the internet throughout the session. Splashtop is not stealthy, users will see a notification indicating the connection is active.
Pros:
- Allows real-time screen sharing and device control
- Useful for IT support and troubleshooting
Cons:
- Requires both devices to have the app installed
- Not discreet; visible notifications alert the user
Use this method only when transparency is acceptable or the person knows.
2. Google Find My Device / Apple Find My iPhone

These official tools are designed to help you locate, lock, or erase lost or stolen devices. With Google Find My Device (for Android) and Apple Find My iPhone (for iOS), you can see the device's location on a map, play a sound to find it, or remotely wipe data to protect privacy.
These services are free, secure, and built into the devices. However, they only offer limited control, and no access to messages, call logs, or app activity.
Pros:
- Official, secure, and free to use
- Effective for locating lost or stolen devices
Cons:
- Requires login credentials for Google or iCloud account
- Limited to location tracking and basic device management
3. Access via Google Account (Android Only)

If you know the target's Google account login information, you can access various data synced to their account without needing physical access. This includes search history, app usage statistics, and location history via Google Maps Timeline.
While this doesn't provide real-time monitoring of messages or social media, it can offer valuable insights into the user's habits and whereabouts, all accessible through any web browser.
Pros:
- No app installation required
- Provides background info like location and search history
Cons:
- Requires knowing the Google account credentials
- Limited to synced data; no live messaging or social media monitoring
Is It Legal to Access Someone's Phone without Their Knowledge?

It's a serious question, and the answer depends on who the person is and why you're doing it. Accessing someone's phone without consent is illegal in many cases unless:
- You are the legal guardian of the person (like a parent).
- You own the phone (such as a company-issued device).
- You have permission or share an account.
In most countries, spying on a partner or stranger without their consent can lead to legal trouble. Always double-check the law in your area before taking any steps.
Risks and Ethical Concerns about Accessing Someone's Phone without Them Knowing

Monitoring someone's phone without their consent can lead to serious legal and ethical issues. Always keep these points in mind:
- Authorization: Ensure you have clear permission or a legitimate reason, like parental supervision or device recovery.
- Data Privacy: Handle any sensitive information carefully and avoid sharing or exploiting it.
- Respect Boundaries: Consider the impact on trust and relationships before invading someone's privacy.
Even if your intentions are good, choosing the right method and respecting legal limits is essential to avoid harm or legal trouble.
FAQs on How to Access Someone's Phone without Them Knowing
Below are some of the most frequently asked questions about how to access someone's phone without them knowing answered clearly to help you make informed decisions.
1. Is it legal to access someone's phone without their permission?
Accessing someone's phone without consent is generally illegal unless you're a parent monitoring a minor child or have legal ownership of the device.
In many regions, unauthorized access can result in criminal charges, including invasion of privacy and data theft. Always ensure you are complying with local laws and use monitoring tools responsibly.
2. Will the target user be notified if their phone is being monitored?
With reliable stealth monitoring tools like SafeMyKid, the monitoring happens in the background and is invisible to the user.
These apps are designed to avoid triggering notifications or system alerts, ensuring the user remains unaware. Still, users may notice performance changes if an unreliable tool is used.
3. Do I need physical access to install a tracking app?
For Android devices, yes, you typically need brief physical access to install the monitoring app and grant necessary permissions. For iPhones, however, apps like SafeMyKid may offer cloud-based monitoring using iCloud credentials, eliminating the need to access the device physically.
4. Can I access someone's phone location in real time?
Yes, real-time GPS tracking is a core feature in most modern monitoring apps. Tools like SafeMyKid allow you to view live location data, set geofences, and receive alerts when the target enters or exits a specified area.
5. What happens if the monitored phone is turned off or not connected to the internet?
If the phone is off or offline, the monitoring tool cannot send or update data until the device reconnects to the internet. Once it's back online, most tools, including SafeMyKid sync any missed activity or logs, ensuring no data is lost during the downtime.
6. Is it possible to monitor social media apps like WhatsApp or Snapchat?
Yes, depending on the tool and device, monitoring social media apps is possible. SafeMyKid and similar apps can track activity on platforms like WhatsApp, Facebook, Instagram, and Snapchat, showing messages, calls, and timestamps.
7. How can I ensure the monitored data remains secure and private?
Use only trusted and encrypted platforms like SafeMyKid, which offer data encryption and secure user dashboards.
Avoid free or unverified tools, as they may compromise sensitive information or even steal it. Always set strong passwords and update software regularly to prevent data breaches.
Conclusion
There are several methods available for those wondering how to access someone's phone without them knowing, but it's important to understand that not all approaches are safe.
For parents, guardians, or employers with a legitimate reason, using a tool like SafeMyKid provides a reliable, secure, and discreet way to monitor a device.




