How to Keylog an iPhone: 7 Proven Methods

With iPhones being among the most secure smartphones on the market, finding a reliable and discreet method to monitor activity on them can be quite challenging.
It's important to choose methods that actually work. In this guide, we'll explore 7 real and effective ways on how to keylog an iPhone safely and legally.

How Does a Keylogger Work on iPhone?
To understand how a keylogger works on an iPhone, it's important to note that iOS is a highly secure operating system with strict sandboxing, meaning apps can't access data from other apps easily.
Because of this, traditional keyloggers which capture every keystroke typed don't work the same way on iPhones as they do on computers or Android devices.
Instead, most iPhone-compatible keyloggers work by:
- Accessing iCloud Data: Many monitoring apps use the target user's iCloud credentials to extract logs, messages, notes, and synced data. While this doesn't record every keystroke, it can effectively capture typed content from messages, emails, and app activity.
- Using Accessibility Features: Some advanced spy apps simulate keylogging by capturing input from specific fields or using screen recording snapshots whenever someone types on the device.
- Monitoring Clipboard Activity or Screenshots: Some tools detect what's copied/pasted or periodically capture screenshots during active app use to infer typed content.
For jailbroken iPhones, true keyloggers can be installed at the system level, offering more traditional keylogging features, but this process involves major risks and voids the device warranty.
7 Effective Ways to Keylog an iPhone
Before diving into each method, note that Apple's security makes keylogging a challenge, especially without jailbreaking. These solutions range from cloud-based tools to physical access options.
1. Use SafeMyKid for Remote iPhone Keylogging

One of the most effective and reliable tools for keylogging an iPhone is SafeMyKid. Unlike other apps, SafeMyKid does not require installation on the iPhone which is ideal for Apple's tightly locked ecosystem.
It works by syncing with the target iPhone's iCloud backup, allowing you to view keystrokes, messages, app activity, and even social media interactions, all without ever touching the device.
Main Features of SafeMyKid for iPhone Keylogging
If you're looking for a reliable way to track keystrokes on an iPhone without physical access, SafeMyKid offers one of the most discreet and effective solutions available.
It operates remotely through iCloud integration, making it suitable for parents who want to monitor their child's digital behavior without alerting them.
- No Installation Required on iPhone: SafeMyKid works via iCloud sync, so there's no need to install anything on the target device. This minimizes detection risk and ensures seamless setup.
- Stealth Mode: The tool runs silently in the background with no app icon, alerts, or visible signs, perfect for keeping monitoring invisible.
- Real-Time Keystroke Tracking: The system captures keystrokes through synced backup data, allowing you to view typed messages, searches, and notes as they happen.
- View Texts, Chats, Emails, and Even Deleted Messages: Gain access to a full range of typed communication, including SMS, iMessage, WhatsApp, email content, and even deleted entries, if recently backed up.
How to Use SafeMyKid for iPhone Keylogging
Setting up SafeMyKid for iPhone keylogging is simple and doesn't require physical access to the device. Once you're signed up and connected through iCloud, the tool works silently and continuously in the background.
Step 1. Create a SafeMyKid Account
Go to the SafeMyKid website and register for an account using your email address.

Step 2. Enter iCloud Credentials of The Target iPhone
Log in to your SafeMyKid dashboard and provide the iCloud username and password linked to the target device.
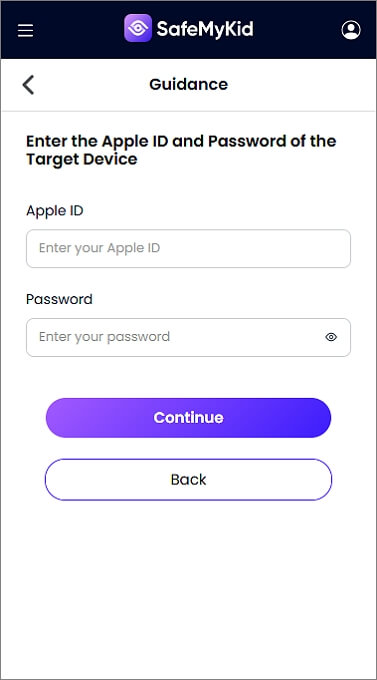
Step 3. Start iPhone Keylogging
SafeMyKid will begin retrieving keystrokes, messages, and app activity from iCloud. You can log in anytime to your dashboard to view real-time logs, chats, emails, and more.
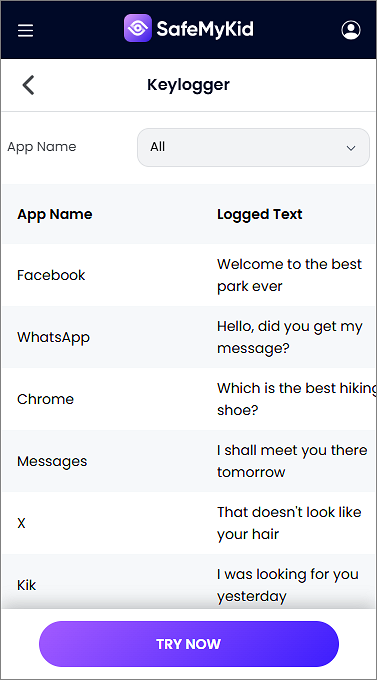
SafeMyKid stands out because of its reliability, ease of use, and legal compliance. Unlike risky spyware or shady apps, this tool is trusted by parents and employers alike.
Other tools like XNSPY or mSpy exist, but they often come with heavier installation requirements and privacy risks.
2. Jailbreaking The iPhone to Install Keylogger Apps

Jailbreaking an iPhone removes Apple's built-in software restrictions, allowing third-party apps (including keyloggers) to be installed via repositories like Cydia.
While this unlocks powerful customization and monitoring tools, it also opens the door to significant risks. Apple continually updates iOS to patch jailbreak exploits, making this method less accessible and more detectable over time.
Pros:
- Full access to install powerful keylogger apps
- Greater control over the device's system and permissions
Cons:
- Voids the device's warranty permanently
- Increases vulnerability to malware and unauthorized access
- Easily detected by tech-savvy users or Apple diagnostics
Apps from repositories like Cydia can capture keystrokes, but jailbreaking is increasingly harder and riskier due to Apple's regular patching.
3. Using MDM (Mobile Device Management) Profiles

MDM profiles are typically used by schools and businesses to control and monitor iPhones remotely.
While they don't offer full keystroke logs, some configurations allow detailed usage tracking that can indirectly reveal typed data through monitored inputs and app behaviors. However, the profile is clearly visible to the user in the settings menu.
Pros:
- Legal for corporate and educational use
- Allows device restrictions, usage monitoring, and partial activity insight
Cons:
- Not stealthy——users can easily see and remove the profile
- Limited in data depth (often no true keystroke capture)
- Only viable for company-owned devices
4. Remote Spyware with Built-in Keyloggers

Some remote spyware apps claim to offer real-time keylogging features along with GPS tracking, SMS monitoring, and app usage insights.
They often disguise themselves as parental control tools. These apps typically require installation and may ask for jailbreak-level access, reducing stealth and increasing risk.
Pros:
- Centralized dashboard to monitor multiple data points
- Some offer cloud-based logs and automatic updates
Cons:
- Many are flagged as malware by antivirus programs
- Often illegal if installed without consent
- Typically, they do not work on iPhones unless jailbroken or protections are bypassed
5. Manual Installation with Physical Access
If you can unlock the iPhone, you might install a monitoring app or sync it with a service like SafeMyKid using the device's iCloud credentials.
This method is most common for parental use, where legal access is typically granted.
Pros:
- Direct installation means more control and setup flexibility
- Legal and effective in parenting scenarios
Cons:
- Requires physical access and screen unlock
- May alert the user via app visibility or sync messages
- Limited to users with proper access rights
6. Experimental Shortcuts or Accessibility Exploits

Reddit users occasionally attempt to use iOS features like Apple Shortcuts or Accessibility settings (such as screen recording or voice control logs) to simulate keylogging.
These are experimental, DIY-style hacks that rarely work reliably, especially with newer iOS updates.
Pros:
- Doesn't require third-party apps
- Can be tested without jailbreaking or extra tools
Cons:
- Unreliable and often outdated after iOS updates
- Easy for the user to spot or disable
- Doesn't capture actual keystrokes in most cases
7. Using Screen Captures Instead of Keystrokes
Rather than capturing typed content, some tools take periodic screenshots and track app activity.
Over time, this can build a profile of the user's actions, even if exact keystrokes are missed. This method focuses on behavioral tracking instead of direct logging.
Pros:
- No need for deep system access or jailbreak
- Can still reveal message content and app usage
Cons:
- Consumes significant storage and bandwidth
- Doesn't capture inputs from hidden fields like passwords
- Misses fast or ephemeral interactions like quick messages
Why Would Someone Want to Keylog an iPhone?

Keylogging an iPhone can serve legitimate and practical purposes when done ethically and legally. Some of the most common reasons include:
- Parental Control: Parents may use keyloggers to monitor their children's texting habits, app use, or online behavior to protect them from cyberbullying, predators, or harmful content.
- Employee Monitoring: Employers may keylog company-owned devices to ensure productivity and prevent data leaks or misuse of resources——provided this is stated in employment policies.
- Relationship Transparency: In cases of mutual agreement, couples might install keylogging tools to rebuild trust after breaches or maintain open digital communication.
- Personal Backup or Security: Some people use keyloggers to back up typed data or track personal activity in case of theft, data loss, or unauthorized device access.
However, it's important to remember that unauthorized keylogging can be considered a serious invasion of privacy and may be illegal. Always get informed consent if the target phone doesn't belong to you or your child.
Is It Legal to Keylog an iPhone?

It depends on your intent and consent. Keylogging someone else's iPhone without permission is illegal in many countries. However, it is legal if:
- You're the parent or legal guardian of the child
- The iPhone belongs to your business or company
- The user gives explicit consent
Violating someone's privacy can result in serious legal consequences. Always use tracking tools like SafeMyKid responsibly and ethically.
How to Tell If a Keylogger Is Installed on Your iPhone
While iPhones are generally secure, some sophisticated keyloggers can still find their way in, especially if someone had physical access to your device or used your iCloud credentials. Recognizing the signs early is important for protecting your data and privacy.
Some common warning signs include:
- Sudden Battery Drain: Keyloggers often run silently in the background, which can cause your battery to deplete much faster than usual.
- Overheating: If your phone gets unusually hot during idle times, background monitoring apps may be running.
- Unexpected App Behavior: Random crashes, screen flickering, or apps behaving strangely may suggest hidden software interfering with your system.
- High Data Usage: Some keyloggers sync logs to remote servers. If your data usage spikes without explanation, it could be a red flag.
- New Configuration or MDM Profiles: Go to Settings > General > VPN & Device Management to check for unknown profiles that may have been installed to manage your device remotely.
Always enable two-factor authentication and regularly update iOS to reduce vulnerability to spyware or keyloggers.
FAQs on How to Keylog an iPhone
To help clear up some common questions and concerns about how to keylog an iPhone, we've put together this FAQ section.
Whether you're curious about performance, privacy, or technical details, these answers will give you a better understanding before you decide which method is right for you.
1. Can keylogging affect the performance of an iPhone?
Keylogging software, especially if poorly designed or resource-heavy, can slow down your iPhone, cause battery drain, or increase data usage. However, reputable services like SafeMyKid are optimized to run discreetly with minimal impact on device performance.
2. How often does SafeMyKid update the keystroke logs from iCloud backups?
SafeMyKid typically syncs with the iCloud backup every few hours, depending on the target device's backup frequency. This means you'll get near real-time updates on keystrokes and activity without any noticeable delay.
3. Is jailbreaking necessary to use SafeMyKid on iPhones?
No, SafeMyKid does not require jailbreaking to monitor iPhones. It leverages iCloud backups to track keystrokes and device activity remotely, keeping the phone's warranty intact and avoiding the security risks of jailbreaking.
4. Can I use SafeMyKid to monitor multiple iPhones simultaneously?
Yes, SafeMyKid allows you to manage and monitor multiple iPhones from a single dashboard, making it convenient for parents or employers who need to track several devices at once.
5. What privacy safeguards does SafeMyKid have to protect monitored data?
SafeMyKid uses encryption and secure servers to store monitored data, ensuring that sensitive information remains private and protected from unauthorized access. User data is only accessible to the account holder.
6. Can SafeMyKid detect deleted messages or keystrokes?
Yes, by syncing with iCloud backups, SafeMyKid can often recover and display deleted messages and keystroke data, provided the backups contain this information before deletion.
7. Are there any limitations if the iPhone's iCloud backup is disabled?
If iCloud backup is disabled or the user frequently clears backups, SafeMyKid's ability to retrieve keystrokes and activity will be limited. Regular iCloud backups are essential for the tool to work effectively.
8. How does SafeMyKid handle encrypted messaging apps like WhatsApp or Signal?
SafeMyKid can track metadata and keystrokes related to encrypted apps if that data is captured in the iCloud backup. However, the content of end-to-end encrypted messages may not always be fully accessible due to encryption protocols.
Conclusion
Now you know exactly how to keylog an iPhone using 7 reliable and proven methods. It's important to use these tools ethically and always stay within legal and privacy boundaries.
While some options can be complicated or involve security risks, tools like SafeMyKid stand out as the most practical, legal, and user-friendly solution available.




