Curious about How to Clone Someone’s Phone? Try These 6 Real Techniques

Have you ever wondered how to clone someone’s phone? Whether you need to monitor a loved one or track a lost device, cloning a phone can be useful. However, not all methods are safe.
In this guide, we will break down how to clone someone’s phone without them knowing, covering 7 powerful methods, including the most reliable and undetectable solutions. Let’s dive in!
What Is Phone Cloning?
Phone cloning refers to duplicating a phone’s data, SIM information, or even entire functionality onto another device. This can be done in multiple ways, including software-based cloning, SIM duplication, or remote access tools.
There are two main types of phone cloning:
- Hardware-based cloning: Involves duplicating a phone’s physical SIM card or copying data through specialized devices.
- Software-based cloning: Uses apps and online tools to clone someone’s Android phone or iPhone remotely.
Is It Possible to Clone Someone's Phone?
Yes, cloning someone’s phone is possible, but the method depends on access level and technical skills. Some require physical access, while others can be done remotely. However, modern security features (like two-factor authentication) make unauthorized cloning difficult.
Challenges & Risks
While phone cloning is technically possible, it’s important to consider the risks and challenges involved in the process. Below are the key challenges and risks that accompany phone cloning:
- Legal Issues: Unauthorized cloning is illegal in many countries.
- Security Measures: Newer devices have anti-cloning protections in place.
- Detection Risks: Some methods leave digital traces, making it easy for the target to detect them.
Despite these challenges, several legitimate and effective ways exist to clone someone’s cell phone without them knowing. Let’s explore them.
Common Uses of Phone Cloning
Phone cloning can serve various purposes, both legitimate and illegitimate. Here are some common uses of cloning someone’s phone:
- Parental Control: Parents may clone their child’s phone to monitor online activity, ensure safety, and prevent exposure to inappropriate content. This is a widely used method for keeping track of their child's digital footprint.
- Data Backup & Recovery: Cloning a phone allows for a seamless transfer of all data to a new device, including contacts, photos, apps, and messages. This method is particularly helpful when switching phones or recovering lost data.
- Unauthorized Surveillance: While phone cloning is sometimes used for legal purposes, it can also be misused for spying on someone without their consent. This type of surveillance is typically illegal and can result in severe consequences for those who engage in it.
6 Ways to Clone Someone's Phone
When considering methods to clone someone's phone, it's important to choose reliable and secure options that minimize risk. Below are seven ways to clone a phone effectively, ensuring you understand each method’s potential:
1. SafeMyKid – The Best Phone Cloning Solution
If you need to clone someone’s phone without them knowing, SafeMyKid is the most effective, stealthy, and legal method available. Unlike spyware, this parental control tool ensures secure and ethical monitoring.

SafeMyKid provides advanced features for monitoring and cloning a phone’s activity without being intrusive. It operates discreetly in the background, tracking calls, messages, location, and app usage.
Designed with security in mind, SafeMyKid ensures that no personal data is compromised during its usage.
Why SafeMyKid Is the Best Choice to Clone Someone’s Phone
SafeMyKid stands out as the best choice for phone cloning due to its advanced monitoring capabilities, user-friendly interface, and ethical design. It provides a seamless and secure solution.
Features that make SafeMyKid the best for phone cloning include:
- Undetectable: It runs in stealth mode on Android devices, ensuring discreet monitoring.
- Remote Monitoring: Access call logs, text messages, GPS location, and app usage in real time.
- Easy to Use: No complex setup is required—simply install and start tracking.
- Multi-Device Compatibility: Works across various operating systems, including iOS and Android.
- Live Updates: Get real-time notifications about activities on the cloned device.
- Secure & Legal: Designed for parental control and responsible monitoring, complying with privacy laws.
With these features, SafeMyKid provides an efficient and ethical way to clone a phone while prioritizing data security and user privacy.
How to Use SafeMyKid to Clone Someone’s Phone without Touching It
Before cloning a phone, it's essential to choose a reliable and secure method that ensures seamless monitoring while maintaining ethical considerations. SafeMyKid offers a user-friendly solution for both Android and iPhone users, making the process simple and effective.
How to Clone Someone’s Android
Step 1. Create an account on SafeMyKid.

Step 2. Install The SafeMyKid App
Download and install the app on the target Android phone. Follow the on-screen instructions to enable monitoring features.
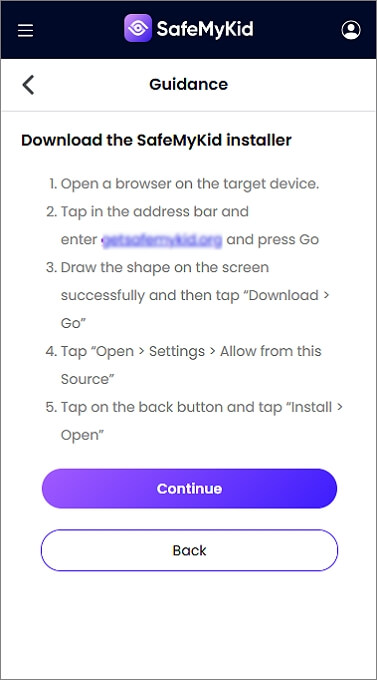
Step 3. Clone Someone’s Android without Touching It
View calls, messages, GPS location, and app activity from your SafeMyKid dashboard.
How to Clone Someone’s iPhone
Step 1. Register for a SafeMyKid account

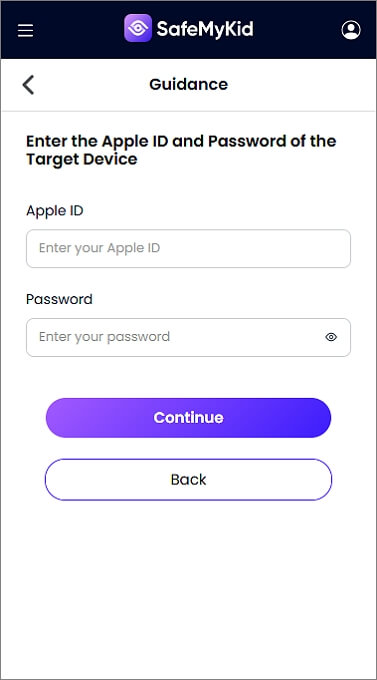
Step 2. Enter iCloud Credentials
No installation is needed –simply enter the target’s iCloud credentials.
Step 3. Clone Someone’s iPhone without Touching It
Access all messages, call logs, and more on your SafeMyKid dashboard.

SafeMyKid is the most reliable way to monitor a phone remotely and discreetly, ensuring you have full access to essential data without detection!
2. Phone Cloning Apps
Many official apps allow users to duplicate phone data seamlessly. Designed primarily for transferring files between devices, these apps can also be repurposed for phone cloning. Popular options include Cloneit, Dr.Fone, and Phone Clone, which offer quick data replication.
Examples:
- Huawei Phone Clone (for Huawei devices)
- Samsung Smart Switch (for Samsung devices)
Pros:
- Easy to use
- No technical skills required
- Transfers all data
Cons:
- Requires physical access
- Cannot monitor real-time activities
3. Cloning a Phone Without Touching It via Spyware

Some spyware apps claim to clone someone’s phone without touching it. These tools often use cloud-based syncing or some tactics to gain entry. However, most require login credentials, making them difficult to use without the target’s knowledge or consent.
Pros:
- Works remotely
- Can monitor real-time activity
Cons:
- Often expensive
- Can be illegal
4. SIM Card Cloning

SIM cloning duplicates the target SIM card’s IMSI and authentication key onto a blank SIM, enabling access to calls, texts, and some data. However, modern encryption and security measures make this method difficult and often illegal in many regions.
How It Works:
- Extract IMSI and authentication key from the SIM.
- Program the information onto a blank SIM.
- Use the cloned SIM to receive calls and messages.
Pros:
- Can intercept texts and calls
- Works on older devices
Cons:
- Requires physical access
- Modern SIM encryption makes it difficult
5. Cloning via Backup & Restore

Cloning via backup and restore involves accessing the target’s iCloud or Google account and restoring their data onto another device. This method can replicate messages, call logs, and app data, but it requires login credentials and may trigger security alerts.
Pros:
- Works for full data transfer
- No hacking required
Cons:
- Needs login credentials
- Doesn’t work in real-time
6. Bluetooth Hacking

Bluetooth hacking exploits security flaws in Bluetooth connections to access a target device. If the phone has an active and unprotected Bluetooth connection, hackers can intercept calls, messages and even clone someone’s cell phone number.
Pros:
- Can capture call logs and messages
Cons:
- Short rangeonly (within 30 feet)
- High failure rate
Comparing Official and Third-Party Phone Cloning Methods
When it comes to cloning someone’s phone, there are two primary approaches: official methods provided by device manufacturers and third-party solutions that claim to offer cloning capabilities.
Understanding the differences between these methods can help determine the most effective and secure option.
Official Methods of Cloning Someone’s Phone: Pros and Cons
Many smartphone manufacturers provide built-in cloning tools, such as Huawei Phone Clone and Samsung Smart Switch, which allow users to transfer phone data safely. These methods are designed for legitimate purposes, such as upgrading to a new device.
Pros:
- Legal and Safe – No risk of violating privacy laws.
- No Extra Costs – Free to use with compatible devices.
- Comprehensive Transfer – Moves contacts, photos, apps, and settings.
Cons:
- Requires Physical Access – The original phone must be in hand.
- Limited Functionality – It doesnot allow real-time monitoring or call/message tracking.
Third-Party Methods: Pros and Cons
Third-party methods offer some features that official methods do not offer, and those have more advantages than official methods. Let's see some of these:
- Ease of Use– Many third-party cloning apps offer simple interfaces, making the process accessible to non-technical users.
- Wide Compatibility– These tools often support multiple devices, including Android and iOS.
- Comprehensive Data Transfer– Some apps allow the cloning of contacts, messages, call logs, and media files.
Many third-party cloning apps promise quick and easy access to another phone’s data, but they often come with severe drawbacks:
- Data Breaches– Unsecured apps can expose sensitive information to hackers.
- Legal Issues– Unauthorized cloning may violate privacy laws, leading to penalties.
- Hidden Costs– Some “free” apps require paid subscriptions to unlock full features.
- Device Security Risks– Many third-party apps can be flagged as malware, leading to detection and removal.
When considering phone cloning, it is crucial to weigh the risks and opt for legal, ethical solutions.
How to Protect Your Phone from Being Cloned
As methods to clone someone’s phone become more advanced, taking proactive security measures is essential to safeguard your personal data. Here are some effective ways to protect your phone from unauthorized cloning:
- Enable Two-Factor Authentication (2FA)– Adding an extra layer of security ensures that even if someone gets your credentials, they won’t be able to access your account without the second authentication step.
- Check Device Settings Regularly– Monitor connected devices and active sessions in your phone settings to spot any suspicious activity. Remove unfamiliar devices immediately.
- Avoid Public Wi-Fi for Sensitive Tasks– Public networks are often unsecured, making them easy targets for hackers who use them to intercept login credentials or inject malware.
- Use Anti-Spyware Tools– Security apps can detect and remove spyware that may have been installed to track your activities remotely.
- Limit Bluetooth and NFC Access– Disable Bluetooth and NFC when not in use to prevent unauthorized data extraction through wireless hacking methods.
- Monitor Account Activity– Regularly check your email, social media, and cloud storage for unusual login attempts, which could indicate someone trying to access your data.
By implementing these precautions, you can significantly reduce the risk of phone cloning and keep your personal information secure.
FAQs on How to Clone Someone's Phone
Before attempting phone cloning, it’s important to understand the legal, ethical, and technical aspects involved. Below are some frequently asked questions about phone cloning.
1. Can I clone someone's phone for free without them knowing?
Yes, but cloning someone’s phone without them knowing for free is extremely difficult. Free methods, such as restoring backups from Google Drive or iCloud, require access to the target's credentials.
Most free apps claiming to clone a phone without access are scams or ineffective. Reliable options like SafeMyKid provide secure, undetectable phone monitoring, but they require a paid plan.
2. How do I clone someone's Android phone without touching it?
Cloning someone’s Android phone without touching it is challenging due to security updates that prevent remote access. However, parental control apps like SafeMyKid allow remote monitoring once installed on the target device.
3. What happens if someone clones my phone number?
If someone manages to clone your phone number, they can receive your calls and text messages, making it possible for them to bypass two-factor authentication (2FA). Signs of phone number cloning include:
- Inability to send/receive texts and calls
- Unknown devices listed under your account
- Unusual login notifications
To prevent this, contact your mobile carrier and enable SIM card lock (PIN protection).
4. How can I clone someone's WhatsApp on my phone?
To clone someone’s WhatsApp on your phone, you can use:
- WhatsApp Web or Linked Devices– If you have temporary access to their phone, scan the QR code on WhatsApp Web to mirror their chats.
- Backup Restoration– If you know their Google or iCloud credentials, you can restore their WhatsApp chat history to another phone.
- Monitoring Apps (SafeMyKid)– SafeMyKid can track WhatsApp activity on Android by logging messages and app usage remotely.
5. Is cloning someone's phone illegal?
Yes, in most cases, cloning someone's phone without their permission is illegal and can result in legal consequences. However, using parental monitoring apps like SafeMyKid to supervise your child’s phone or backing up your own device is legal.
6. Can I clone someone's cell phone without installing software?
It depends on the method. Cloning someone’s cell phone without installing software is only possible if you have access to their iCloud, Google, or carrier account. For example:
- iPhone cloning via iCloud requires login credentials but no app installation.
- SIM cloning requires physical access but no software.
- For Android, an app like SafeMyKid must be installed for effective monitoring.
7. What is the best way to clone someone's phone remotely?
The best way to clone someone’s phone remotely is to use a trusted monitoring app like SafeMyKid. Unlike unreliable free apps, SafeMyKid ensures a secure and ethical way to monitor a phone remotely.
Conclusion
Now that you know how to clone someone's phone, it’s clear that SafeMyKid is the best and safest solution. While other methods exist, they often require physical access or pose legal risks.
If you need a discreet, reliable, and powerful way to monitor a phone, SafeMyKid is your best option. Just be sure to use any cloning method responsibly and within the law!




