Phone Hacked? These 6 Secret Phone Hacked Codes Reveal If You’re Being Watched

Have you ever wondered if someone might be spying on your calls, messages, or even your location? If so, that's where phone-hacking codes come in; they're dial codes you can use to detect if your phone is being monitored.

These codes allow you to check whether your phone is being redirected, tapped, or otherwise compromised. In this article, I'll introduce you to 6 of the most commonly used phone hacking codes.
What are Phone Hacked Codes?
Phone-hacked codes are special dialer commands, often USSD or MMI codes, that reveal hidden settings or activities on your phone. These codes can help you detect signs of unauthorized access, such as call forwarding, message redirection, or remote surveillance.
By simply dialing a specific combination like *#21# or *#62#, you can check if your calls, texts, or data are being rerouted without your consent.
These codes work on most Android and iOS devices and are especially useful for identifying possible security breaches or phone tapping.
6 Dial Codes to Check If Your Phone Is Hacked
Let's walk through six trusted phone hacking codes. These work differently on Android, iPhone, and sometimes Samsung-specific models. Use them wisely.
1. #21# —— Check for Call Forwarding
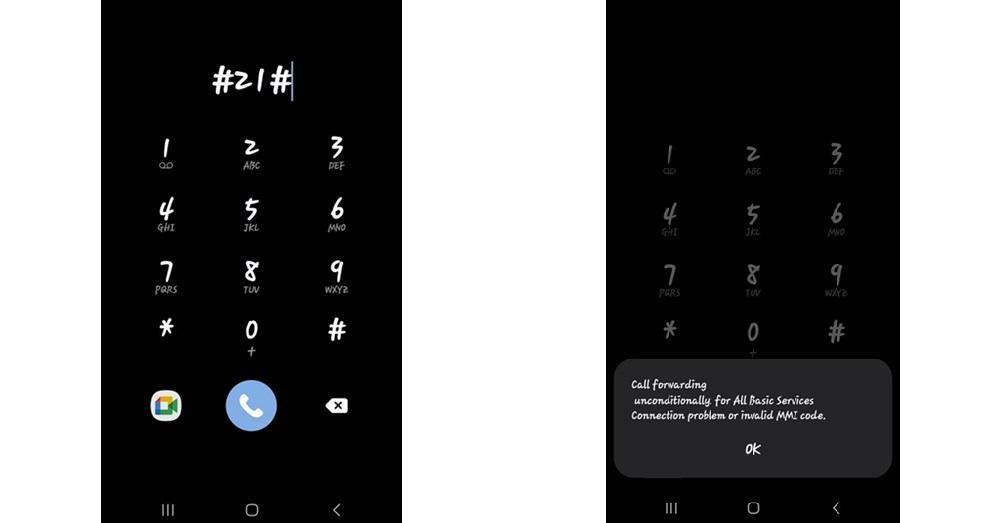
The ##21# USSD code is a straightforward method to verify whether your calls, SMS, and data are being forwarded to another number without your knowledge. Hackers or malicious actors sometimes use call forwarding to intercept voice calls and messages.
When you dial this code, your screen will show if any service (voice, SMS, data, fax, etc.) is currently being redirected. If it says "Not Forwarded", you're generally in the clear. If you see a number listed, especially one you don't recognize, your line might be compromised.
Pros:
- Instant result, no need for apps or third-party tools.
- Works across carriers and most phone models.
- Helps confirm if someone has tampered with network-level settings.
Cons:
- Only detects forwarding, not hidden apps or remote access.
- Doesn't help if the hacker uses spyware instead of call diversion.
- Limited detection if the forwarding is toggled off remotely after use.
2. #62# —— Forwarding When Unreachable
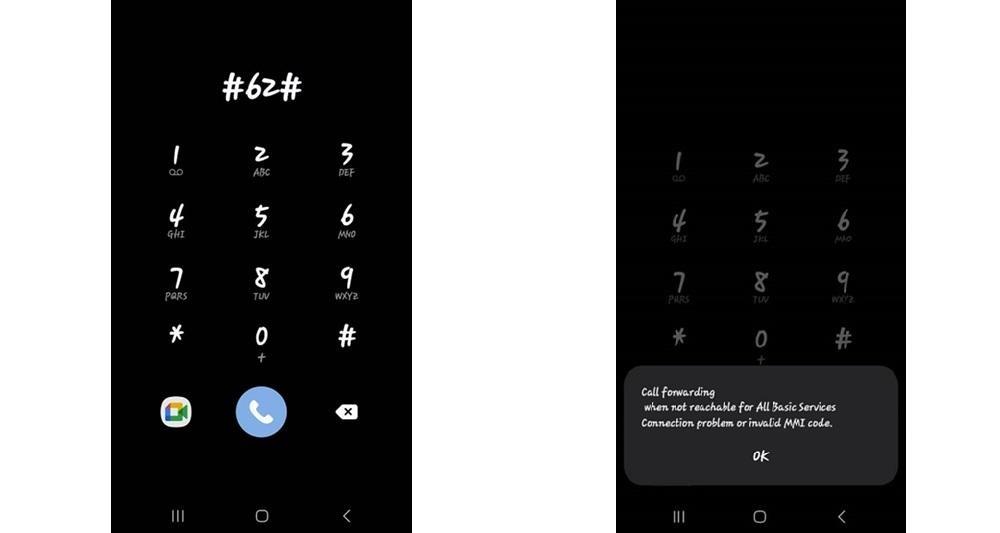
This is another important code to check if your phone is hacked. Dialing ##62# tells you if your phone redirects calls when it's turned off, out of range, or in airplane mode. If a suspicious number appears here, it could be a sign that someone is monitoring your calls.
This method is often used by cybercriminals to avoid detection because most people won't notice call forwarding unless the phone is powered off. If you suspect voice tapping or message redirection, this check is crucial.
Pros:
- Effective for catching subtle, conditional redirection.
- Gives clear details on what happens when your phone is unavailable.
- Helps protect against stalkers or ex-partners who access your device.
Cons:
- Doesn't show forwarding activity when your phone is on.
- Limited to voice-related spying, not apps or data monitoring.
- If you recently reset your phone, the redirection logs may be wiped.
3. #002# —— Deactivate all Call Forwarding
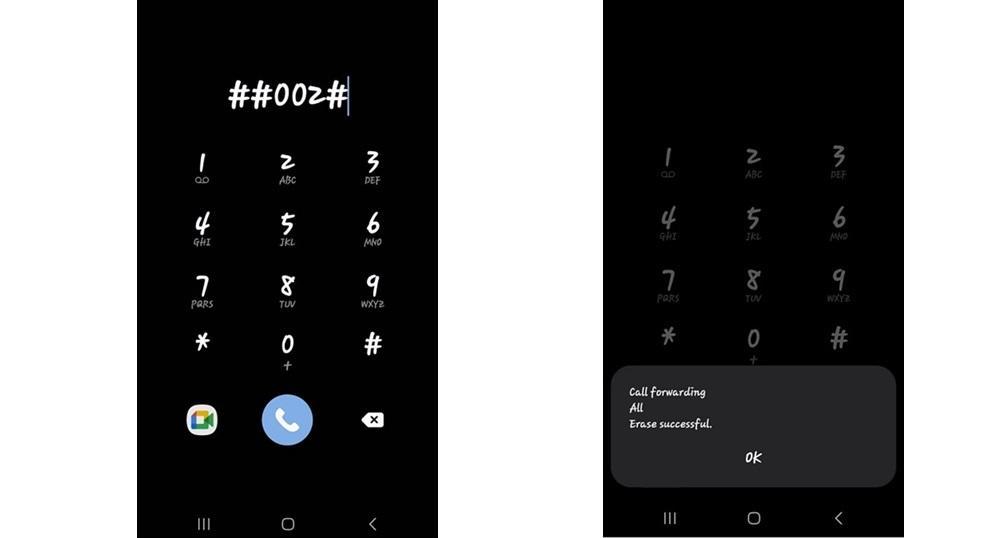
This is the most powerful network-related reset command. When you dial ##002#, you're instructing your mobile network to cancel all forms of call forwarding from your number. It's a key defense if you suspect that someone has tampered with your settings, even temporarily.
It works across most GSM networks and is particularly useful if you've traveled, inserted your SIM into a different phone, or suspect SIM swap fraud. It doesn't alert anyone and gives you peace of mind that no redirection is active.
Pros:
- Universal reset for all types of forwarding (busy, unreachable, no reply).
- Removes both visible and hidden call redirection.
- No app or tech skills required.
Cons:
- Doesn't undo damage caused by malware or spyware.
- If you rely on forwarding yourself (e.g., for work), you'll have to reconfigure it.
- Won't inform you if redirection was happening before dialing it.
4. #06# —— IMEI Check

Dialing *#06# shows your device's IMEI (International Mobile Equipment Identity); a unique number used to identify your phone on any network. While this code doesn't directly check if your phone is hacked, it can help you detect phone cloning.
If your IMEI number has been changed, masked, or is different from what your phone box or documentation shows, someone may be using a cloned version of your device to intercept calls and texts. It's especially important after purchasing secondhand devices.
Pros:
- Fast and works offline.
- Useful for detecting identity theft, especially SIM or phone cloning.
- Critical for filing police reports or blocking lost/stolen phones.
Cons:
- Doesn't reveal spyware or redirection settings.
- Won't alert you to current hacking activity.
- IMEI tampering often requires deeper technical checks to confirm.
5. *#*#44336#*#* —— Android Test Menu

This Android-specific code to check if phone is hacked opens a hidden developer menu that displays phone stats, system uptime, software info, and sometimes even usage history logs. It's designed for engineers and support staff, but savvy users can use it to detect strange activity.
If your phone shows unusually high background activity, unknown system apps, or suspicious installations, this menu can help you spot it, even if the app is hidden from your regular app drawer.
Pros:
- Reveals system-level details not shown in normal settings.
- Useful for detecting suspicious background activity or forced updates.
- Doesn't require root access or developer mode.
Cons:
- Not available on all Android models (Samsung and newer Androids may block it).
- Requires tech knowledge to interpret results accurately.
- No direct indication of spyware, only indirect signs.
6. 3001#12345# —— iPhone Field Test Mode

Field Test Mode is a secret diagnostic tool for iPhones. By dialing *3001#12345#*, you access technical data about your device's connection to the network, including cell tower IDs, signal strength, and tracking metrics.
This is useful for spotting fake cell towers (e.g., IMSI catchers or Stingrays), which may be used to intercept communications. It won't directly tell you if spyware is installed, but it can expose network-level anomalies that suggest surveillance or tampering.
Pros:
- Provides raw carrier and signal data.
- Helps detect unusual network behavior or spoofed signals.
- Useful for advanced diagnostics and carrier verification.
Cons:
- No information on apps or file access.
- It can be confusing for the average user.
- Doesn't work on all iOS versions (especially after iOS 16+ updates).
Signs That Your Phone May Be Hacked

Noticing something unusual? These red flags could mean your phone's been compromised:
- The batterydrains faster than usual
- Phone overheats even when idle
- Strange background noises during calls
- Unknown apps suddenly appear
- You see messages or calls you never sent
These symptoms suggest possible spyware or monitoring software. If you experience any, it's time to try a code to check if your phone is hacked.
What If You Want to Hack Someone's Phone Instead?
While most people are concerned about protecting their own devices, others may be looking for ways to monitor someone else's phone for safety or accountability reasons, especially parents or employers.

Before we jump into the methods, let's talk about SafeMyKid. SafeMyKid is a trusted parental control tool that allows you to legally and discreetly monitor someone's device. It gives you access to messages, location history, call logs, app usage, and more.
Top Features of SafeMyKid That Let You Hack Someone's Phone
If you're looking for a responsible way to monitor another device, especially as a parent or employer, SafeMyKid offers powerful, stealthy tools that provide complete insight without rooting or jailbreaking the phone.
Here are the standout features:
- Live Message Monitoring: Read SMS and popular messaging app conversations (like WhatsApp, Facebook Messenger, Telegram, etc.) in real time, even deleted ones. Great for uncovering hidden chats or suspicious conversations.
- Call Log Tracking: View incoming, outgoing, and missed calls,including timestamps and contact details. Some plans even support audio recording, depending on local laws.
- GPS Location Tracking: Track the target device's real-time location with high accuracy. You can also view historical movement routes, geofences, and get alerts when they enter or exit certain zones.
- Media File Access: View all saved or received photos, videos, and audio files, even those sent through social apps. This includes hidden or deleted media if backups exist.
- Browser & App Activity Log: See which websites they visit and what apps they use the most. Thisgives insight into potential red flags or dangerous habits.
- Social Media Monitoring: Monitor messages sent via Instagram, Snapchat, Viber, and more. You'll know who they're talking to and what's being said.
- Stealth Mode: SafeMyKid runs invisibly in the background, with no app icon and no notifications. The user won't know it's there unless they search system files deeply.
- Keylogger Functionality: Captures every keystroke made on the device, including usernames, passwords, search queries, and typed messages, even those not sent. This is helpful for uncovering login details or confirming secret conversations.
- Remote Screenshot Capture: Take live screenshots of the device remotely. You can visually confirm what the person is doing in real-time, whether browsing certain websites, chatting on an app, or viewing suspicious content.
- Wi-Fi Network History: See every Wi-Fi network the phone connects to. This helps determine the physical location and pattern of movement, including private networks at school, work, or unknown places.
- Alerts for Suspicious Activity: Get notified when specific keywords are used in messages, when the phone enters restricted locations, or when prohibited apps are installed. Custom alerts can be tailored for safety or behavioral monitoring.
SafeMyKid combines these advanced features into one centralized, user-friendly dashboard, giving you unmatched visibility and control without needing root or jailbreak access. These tools provide unmatched digital oversight.
How to Use SafeMyKid to Hack Someone's Phone
Before diving into technical codes or complicated tools, SafeMyKid offers a far simpler, more efficient solution. It gives you full access to someone's phone activity without the limitations of USSD codes or guesswork. Here's how to set it up:
How to Hack an iPhone
Step 1.Sign up for an Account
Head to SafeMyKid's website and register for an account.

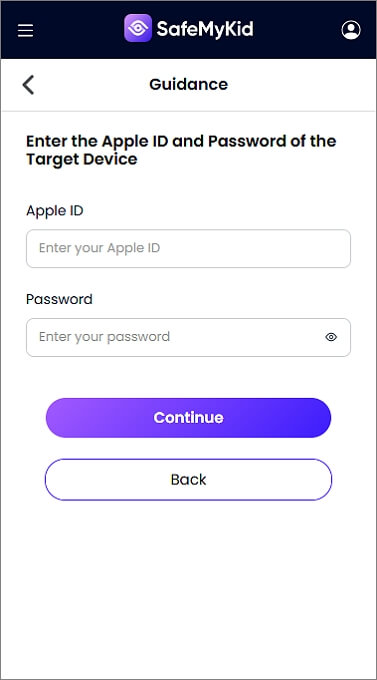
Step 2.Link The iCloud Account of The Target Device
Enter the iCloud credentials of the iPhone you want to monitor. No physical access is needed for iPhones as long as you have the target's iCloud credentials.
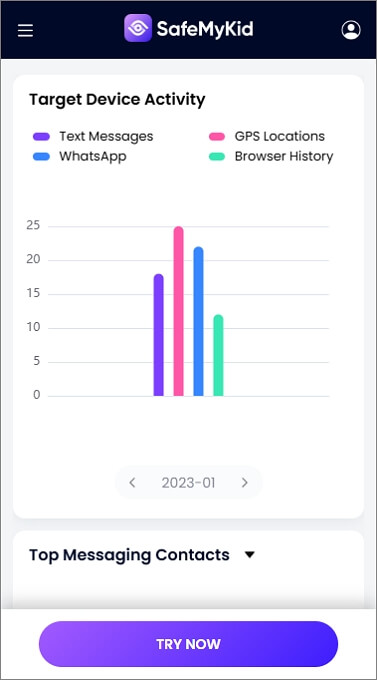
Step 3.Hack an iPhone Remotely
Access all backed-up data, such as messages, call logs, locations, WhatsApp chats, and more, directly from your SafeMyKid dashboard.
How to Hack an Android Phone
Step 1.Create a SafeMyKid Account on The Official Website
Visit SafeMyKid's website and sign up using a valid email.

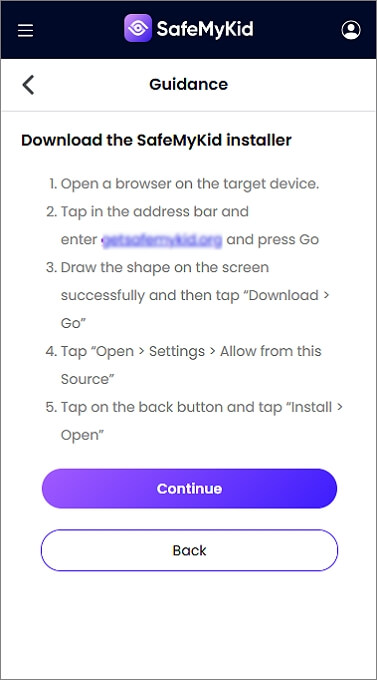
Step 2.Install SafeMyKid on The Target Android Device
Access the Android phone for a few minutes, download the SafeMyKid app, and follow the easy installation wizard.
Step 3.Hack an Android Phone Remotely
Log in to your dashboard from any device. From there, you can read text messages, access social media chats, track calls, monitor keystrokes, and much more.

Unlike the manual phone hacked code, which only checks call forwarding or MMI status, SafeMyKid gives you continuous access to messages, app activity, and location data,making it far more powerful and practical for anyone needing full visibility over another device.
Are These iPhone Hacked Codes Always Accurate?

While iPhone hacked codes such as *#21#, *#62#, or *3001#12345#* provide useful insights into your device's call forwarding and network status, they are not foolproof.
These codes are designed to work within the limitations of your carrier's system, so they only detect network-level compromises like call diversion, not deeper security threats.
If your phone is infected with spyware, stalkerware, or remote access tools, these codes may show everything as "normal", even though your privacy is compromised. That's why many users prefer to use monitoring apps that scan more than just call redirection or basic network activity.
Advantages of Official Phone Hacked Codes:
- Free and fast to use.
- No installation needed.
- Privacy-safe because they don't transmit data.
Disadvantages of Official Phone Hacked Codes:
- Can't detect spyware that doesn't use call forwarding.
- Doesn't reveal which app or tool may be spying on you.
- Some code to check if a Samsungphone is hacked; options may not work on every model or carrier.
They're best for quick checks, but for complete peace of mind, SafeMyKid offers a more advanced solution.
Tips to Prevent Getting Hacked

If you want to avoid using a phone-hacked code in the future, it's best to be proactive. A few smart habits can drastically reduce the chances of your device being compromised.
- Avoid scanning unknown QR codes: They can silently install malware or redirect you to unsafe sites.
- Don't download apps outside Google Play or App Store: Third-party APKs are a common way hackers sneak in spyware.
- Keep your system updated: Security patches fix known vulnerabilities.
- Use 2FA for all logins: It makes it harder for hackers to access your accounts.
FAQs on Phone Hacked Codes
If you still have questions about detecting or preventing phone hacking, you're not alone. Below are some of the most frequently asked questions that offer additional clarity and tips to help you stay protected.
1. Can someone hack my phone without physical access?
Yes, hackers can compromise your phone without ever touching it. Through fake Wi-Fi networks, some apps, or even some QR codes, attackers can install spyware remotely.
2. Will dialing a phone-hacked code notify the hacker?
No, dialing USSD or MMI codes won't notify anyone, including a potential hacker. These codes simply query your mobile carrier or system settings, making them safe and invisible. However, if the hacker is using advanced spyware, they may still have broader access to your activity.
3. Are phone hacking codes the same for all devices?
Not always. While many phone hacking codes are universal, some codes work only on specific devices or brands (like Samsung or iPhone), and certain Android versions may not support every code. Always double-check compatibility before relying on any single code.
4. Is it safe to share my IMEI number with others?
No, sharing your IMEI number publicly can be risky. Hackers can clone your device or blacklist it remotely using this unique identifier. If you've accidentally shared it, contact your mobile provider and keep an eye on your device activity through trusted tools.
5. Can antivirus apps detect if my phone is hacked?
Some antivirus apps can detect basic threats, but many types of spyware are designed to evade traditional scanners.
6. How often should I check my phone using hacked codes?
It's a good habit to check every few weeks or whenever you notice suspicious behavior like fast battery drain, call interruptions, or data spikes.
7. Can hackers use Bluetooth or nearby devices to access my phone?
Yes, if your Bluetooth is left on and your device is discoverable, nearby attackers can attempt to connect or send malicious files. Always turn off Bluetooth when not in use and review your paired device list for unknown entries.
8. Can your phone get hacked by scanning a QR code?
Yes, QR codes can be embedded with malicious links or scripts that, once scanned, redirect you to unsafe websites or initiate automatic downloads. These downloads might contain spyware or keyloggers designed to monitor your activity.
Conclusion
Using a phone's hacked code is a quick and convenient way to spot signs of suspicious activity, like call forwarding or unauthorized access, but it's not always enough.
Whereas, if you want to hack a phone to gain real-time insights, a dedicated tool like SafeMyKid offers very comprehensive monitoring.