How to Get Someone's Phone Records: 6 Proven Methods

The question of how to get someone's phone records has become increasingly relevant as individuals seek to access call logs, text records, and communication histories for legitimate purposes like parental oversight, legal proceedings, or account management.

With proper authorization and the right approach, obtaining phone records can provide crucial information for protecting children, managing business communications, or gathering evidence for legal matters.
Is It Actually Possible to Get Someone's Phone Records?
Yes, obtaining someone's phone records is possible, but with significant legal restrictions and specific requirements:
Legal access typically requires:
- Being the account holder or authorized user on the phone plan
- Court orders or subpoenas for legal proceedings
- Parental authority for minor children's records
- Written consent from the phone user
- Business ownership of company devices
Available information varies by method:
- Carrier records show calls, texts, and data usage
- Monitoring apps provide comprehensive communication logs
- Cloud backups contain message histories and call logs
- Device-based extraction offers complete records
Legal limitations are strict - accessing phone records without proper authorization violates federal and state privacy laws, potentially resulting in criminal charges.
SafeMyKid - The Most Comprehensive Solution to Get Someone's Phone Records

When evaluating solutions for how to get someone's phone records legally, SafeMyKid stands out as the premier monitoring platform for families and organizations with legitimate oversight needs.
SafeMyKid provides unparalleled access to comprehensive phone records through advanced monitoring technology that captures all communication data in real time across Android and iOS devices.
Its sophisticated features extend far beyond basic call logs to include detailed message records, app-based communications, and multimedia exchanges, creating complete communication documentation for authorized users.
Key Features of SafeMyKid to Get Someone's Phone Records
When determining what makes SafeMyKid the optimal solution for obtaining phone records, several distinctive capabilities set it apart:
Complete Call Log Documentation - Access detailed records of all incoming, outgoing, and missed calls with timestamps, duration, contact information, and frequency analysis.
Comprehensive Message Records - Retrieve full-text message histories including SMS, MMS, and iMessage with complete content, timestamps, and participant information.
App Communication Logs - Monitor communications across WhatsApp, Facebook Messenger, Instagram, Snapchat, and other platforms where modern conversations occur.
Deleted Record Recovery - Access phone records that have been deleted from the device, ensuring complete communication history preservation.
How to Get Someone's Cell Phone Records without Them Knowing
Configuring SafeMyKid for comprehensive phone record access requires just a few simple steps:
Step 1. Create Your SafeMyKid Account
Visit the SafeMyKid website to register and establish your secure monitoring dashboard.

Step 2. Configure The Target Device
For iPhones: You can set up call monitoring by logging in with the device's iCloud credentials. No physical app installation is required.
For Android Devices: You'll need to download and install the SafeMyKid app directly on the device you want to monitor (with proper authorization).
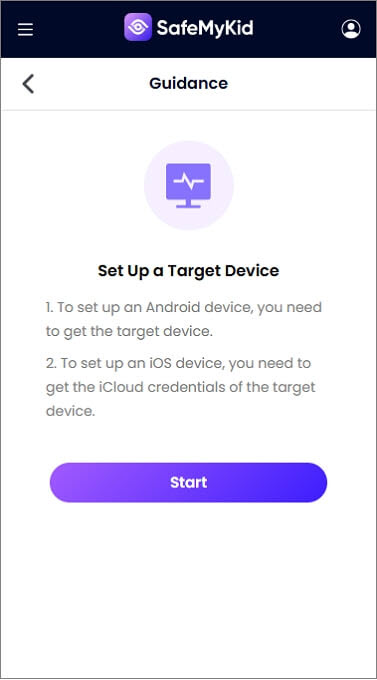
Step 3. Access Complete Someone's Phone Records
Log in to your dashboard to view all phone records, generate reports, and set up alerts for specific communication patterns.
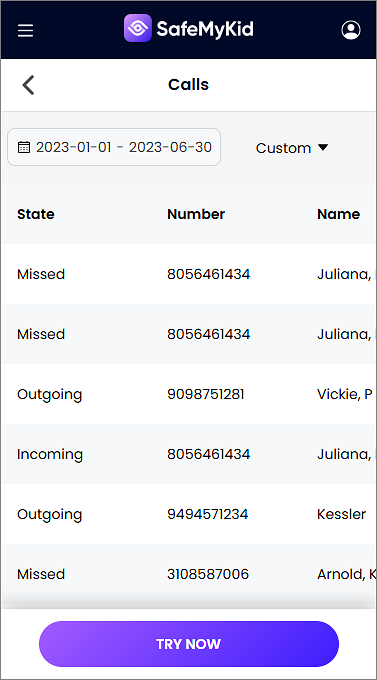
Once properly configured, SafeMyKid provides continuous access to comprehensive phone records, delivering the detailed communication documentation needed for legitimate monitoring purposes.
5 Other Methods to Get Someone's Phone Records
When investigating how to get someone's phone records legally, several approaches exist beyond dedicated monitoring applications. Understanding these methods helps determine which option best suits your specific situation and authorization level.
1. Carrier Account Access

Mobile carriers maintain detailed records of all communications on their networks, making them a primary source when learning how to get someone's phone records through official channels.
Carrier records typically include:
- Complete call logs with numbers, dates, times, and duration
- Text message logs showing sender, recipient, and timestamps
- Data usage records by application and time period
- Location data based on cell tower connections
- International calling and roaming records
To access carrier phone records:
- Log into your online account or visit a carrier store
- Navigate to the billing or usage details section
- Request detailed records for specific time periods
- Download or print records in PDF or CSV format
- Contact customer service for historical records beyond online availability
This method works best when you're the primary account holder or authorized user on the phone plan. Major carriers like Verizon, AT&T, T-Mobile, and Sprint provide varying levels of detail in their records, with some offering up to 18 months of historical data.
The primary limitation is that carrier records show metadata (who called whom and when) but not actual message content or call recordings.
2. Court Orders and Legal Subpoenas
Legal proceedings provide formal mechanisms for how to get someone's phone records when authorized by the court system for legitimate legal purposes.
Legal methods for obtaining records include:
- Civil subpoenas in divorce or custody proceedings
- Criminal investigation warrants
- Discovery requests in litigation
- Administrative subpoenas for regulatory matters
- Court orders for specific record production
The legal process typically involves:
- Filing appropriate motions with the court
- Demonstrating relevance to the legal matter
- Serving subpoenas on carriers or device owners
- Allowing time for objections or compliance
- Receiving records through legal channels
This approach provides the most comprehensive access to phone records, including content that carriers normally don't provide to consumers, such as text message content and detailed location data.
The primary requirement is an active legal proceeding with proper jurisdiction and a legitimate need for the records as evidence.
3. Cloud Backup Extraction
Modern smartphones automatically back up communication data to cloud services, creating another avenue for how to get someone's phone records through account access.
Cloud services storing phone records include:
- iCloud for iPhone call logs and messages
- Google Drive for Android device backups
- Samsung Cloud for Samsung devices
- OneDrive for Windows Phone records
- Third-party backup services
To extract phone records from cloud backups:
- Access the cloud account with the proper credentials
- Navigate to the device backup sections
- Download relevant backup files
- Use extraction tools to parse backup data
- Export records in readable formats
This method proves particularly effective for accessing complete message histories and call logs when you have legitimate access to cloud account credentials, such as parents managing children's accounts or business administrators overseeing company accounts.
The primary limitation is that cloud backups may not include real-time data and require regular backup completion for comprehensive records.
4. Device-Based Extraction Tools
Professional forensic tools provide direct methods for how to get someone's phone records by extracting data directly from the physical device.
Device extraction methods include:
- iTunes backup extraction for iPhones
- Android Debug Bridge (ADB) for Android devices
- Professional forensic software like Cellebrite
- Open-source tools for specific extractions
- Manufacturer diagnostic modes
The extraction process typically involves:
- Physical access to the unlocked device
- Connecting to a computer with extraction software
- Creating a complete device backup
- Parsing communication databases
- Exporting records in organized formats
This approach provides the most comprehensive phone records, including deleted data, app communications, and detailed metadata not available through other methods.
The primary requirements are physical device access and technical expertise to properly use extraction tools while maintaining data integrity.
5. Monitoring Applications

Specialized monitoring applications offer ongoing access to phone records, addressing how to get someone's phone records continuously rather than as a one-time extraction.
Monitoring app capabilities include:
- Real-time call log updates
- Complete message content capture
- App-based communication monitoring
- Multimedia message records
- Browser history and app usage logs
Benefits of monitoring apps:
- Continuous record collection without repeated access
- Cloud-based storage preventing local deletion
- Advanced search and filtering capabilities
- Automated alerts for specific activities
- Professional reporting features
This method suits ongoing monitoring needs, particularly for parental control or consensual relationship monitoring where continuous oversight is necessary.
The primary consideration is that monitoring apps require initial installation and may not capture historical records from before installation.
Why You Might Need to Get Someone's Phone Records
There are several legitimate scenarios where accessing someone's phone records becomes necessary in today's interconnected world.
Parents often need comprehensive phone records to monitor their children's communications, identify potential safety threats, and ensure appropriate phone usage within family guidelines.
Legal professionals may require phone records as evidence in divorce proceedings, custody disputes, criminal investigations, or civil litigation where communication patterns provide crucial documentation.
Business owners might need employee phone records from company devices to verify appropriate usage, investigate misconduct, or comply with regulatory requirements.
Common Misconceptions about How to Get Someone's Phone Records

Several persistent myths surrounding how to get someone's phone records can lead to wasted effort or legal troubles.
Many people believe online services claiming to provide instant phone records for any number are legitimate. These services are invariably scams that cannot deliver actual phone records without proper authorization.
Similarly, the misconception that phone companies freely share records with anyone who calls is false——carriers have strict verification procedures.
Another dangerous myth is that deleted phone records are gone forever. In reality, carriers maintain records for months, and forensic tools can recover deleted data.
Understanding these misconceptions helps focus efforts on legitimate methods to get someone's phone records while avoiding costly mistakes or legal violations.
Types of Information Available in Phone Records
Understanding what phone records actually contain helps set realistic expectations when learning how to get someone's phone records.
Standard carrier phone records include call logs showing numbers, timestamps, duration, and whether calls were incoming or outgoing.
Text message logs display sender and recipient numbers with timestamps but not message content. Data usage records show which apps consumed bandwidth and when.
Enhanced records through monitoring apps or forensic extraction can include actual message content, deleted communications, app-based messaging, voice message transcripts, and multimedia files. Location data may show cell tower connections or GPS coordinates.
Understanding these distinctions helps choose the appropriate method for getting someone's phone records based on what information you actually need for your legitimate purpose.
Frequently Asked Questions about Getting Phone Records
Understanding answers to these common questions helps you obtain phone records legally and effectively:
1. Can I get someone's phone records without them knowing?
If you're the primary account holder, you can typically access basic phone records through your carrier without notifying other users on the account. However, accessing detailed records or message content usually requires either the person's knowledge or proper legal authorization.
2. How far back can I get phone records from carriers?
Most major carriers retain call logs for 12-18 months and text message logs for 3-6 months, though actual message content is typically not stored. Some carriers offer extended record retention for business accounts.
3. Do phone records show deleted messages?
Carrier phone records show that messages were sent or received but don't include content, whether deleted or not. To access deleted message content, you need either cloud backups from before deletion or monitoring software that captures messages in real time.
4. What's the difference between phone records and phone transcripts?
Phone records include metadata like call times, duration, and numbers contacted, plus text message logs. Phone transcripts would include actual conversation content, which carriers don't provide, and would require recording or monitoring software.
5. Can employers legally access employee phone records?
Employers can generally access phone records for company-owned devices if they've provided clear policies about monitoring. However, personal calls and messages may still have privacy protections.
For employee-owned devices used for work (BYOD), employers typically cannot access records without explicit consent or compelling business necessity.
Conclusion
Understanding how to get someone's phone records requires navigating complex legal requirements, technical methods, and ethical considerations. While multiple approaches exist——from carrier access to monitoring applications——each has specific authorization requirements.
For those with legitimate needs like parental oversight or legal proceedings, solutions range from basic carrier records to comprehensive monitoring platforms like SafeMyKid. The key is matching your method to your specific authorization level and information needs.