How to Hack into Someone's iPhone Camera - 6 Methods Explained

Ever wondered how to hack into someone's iPhone camera remotely? The short answer is yes——there are multiple ways someone might attempt to monitor an iPhone camera without direct physical access.

This guide will break down 7 methods explaining how someone might try to hack into an iPhone camera and what you can do to protect yourself.
4 Legal Methods to Monitor iPhone Cameras
When you need to monitor an iPhone camera for legitimate purposes, these methods provide legal and ethical options that respect privacy while fulfilling your monitoring needs.
1. SafeMyKid: The Best Way to Hack into Someone's iPhone Photos Legally

If you need a legal, ethical, and safe way to monitor someone's iPhone photos, the best solution is SafeMyKid.
Unlike spyware and hacking tools that operate secretly and often violate privacy laws, SafeMyKid is a completely legal and ethical parental control app designed to help parents and guardians monitor their children's activities for safety reasons.
It provides secure access to a child's device, allowing parents to track real-time activity, including camera access, without breaking any laws. SafeMyKid ensures that monitoring remains transparent, responsible, and compliant with privacy regulations.
SafeMyKid Features for Accessing iPhone Photos Legally
SafeMyKid is a responsible monitoring tool designed to ensure safety and provide peace of mind for parents and guardians. Here's an expanded list of its features that can help you monitor an iPhone's photos ethically:
- Photo Access: Remotely view real-time photos and video, giving you an instant visual of your child's environment without their knowledge, but only when necessary for safety reasons.
- Discreet Monitoring: SafeMyKid works in the background, ensuring that your monitoring activities remain undetected on the device. This feature ensures privacy while allowing you to keep track of the phone's activities.
- Secure & Legal: The app is built with ethical use in mind, specifically designed for responsible monitoring. It adheres to legal guidelines, ensuring the monitoring remains within the boundaries of parental control and guardianship.
- Remote Control: In case of emergency, SafeMyKid lets you remotely lock or wipe the device to prevent access to sensitive data or to stop potentially dangerous activity.
- Multimedia Data Monitoring: Track installed apps and their usage to ensure there are no harmful applications that could lead to dangerous interactions or privacy breaches.
How to Set up SafeMyKid to Hack Someone's iPhone Photos Legally
Setting up SafeMyKid to monitor someone's iPhone photos is a straightforward process. It's important to follow the steps carefully to ensure proper configuration and ethical use. Here's how to get started:
Step 1. Sign up
Visit the SafeMyKid website and sign up for an account.

Step 2. Enable iCloud Sync
Input the Apple ID and password of the target device to sync information.
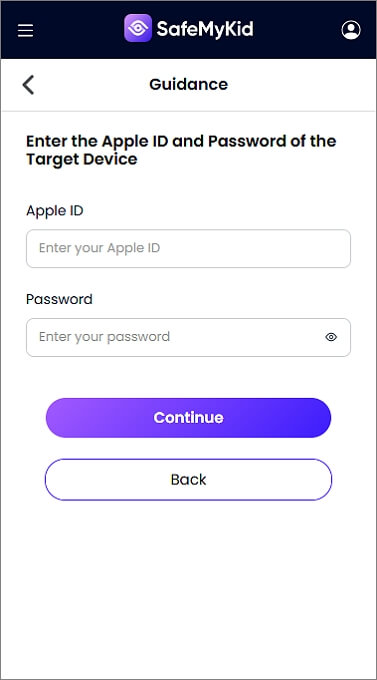
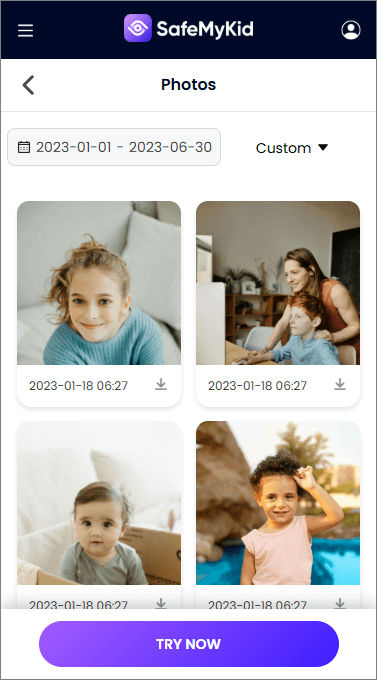
Step 3. Hack into Someone's iPhone Photos Remotely
You can monitor the photos remotely via the SafeMyKid dashboard.
2. Apple's Family Sharing and Screen Time
Apple's Family Sharing with Screen Time provides a comprehensive solution for parents to monitor their children's device usage without third-party applications. This native iOS feature allows families to share purchases while maintaining appropriate oversight.
The system works seamlessly within Apple's ecosystem, offering a transparent approach to monitoring that respects privacy while providing necessary parental controls. Regular updates ensure the system evolves to address new digital parenting challenges.
How It Works:
- Set up Family Sharing with your child's Apple ID
- Enable Screen Time restrictions
- Configure app limits and content restrictions
- Approve app downloads and purchases
Benefits:
- Native iOS integration
- No third-party apps required
- Transparent to all users
- Regular updates from Apple
3. MDM Solutions for Business
Mobile Device Management solutions provide businesses with powerful tools to secure and monitor company-owned iPhones used by employees. These enterprise-grade systems allow for comprehensive policy enforcement.
MDM implementations balance security needs with employee privacy through transparent policies and proper disclosure. When implemented correctly, these systems protect company assets while respecting workforce privacy expectations.
How MDM Works:
- The company installs an MDM profile on the device
- IT administrators can manage security policies
- Camera functionality can be controlled remotely
- Usage policies are enforced systematically
Requirements:
- Must be used on company-owned devices
- Requires proper disclosure to employees
- Should be mentioned in employment agreements
- Needs to comply with privacy regulations
4. Find My iPhone for Lost Devices
Find My iPhone offers basic monitoring capabilities specifically designed to help recover lost or stolen devices. This service focuses on device location and security rather than comprehensive monitoring.
The system prioritizes recovery features while maintaining user privacy, making it unsuitable for ongoing monitoring purposes. Its limited functionality is intentionally designed for temporary use during device recovery situations.
Features:
- Locate the device on a map
- Play a sound to find it nearby
- Put it in Lost Mode to lock it remotely
- Erase all data if necessary
Limitations:
- Doesn't provide camera access
- Focused on recovery, not monitoring
- Requires the device to be online
- Works only with your own devices
2 Methods Hackers Use to Access iPhone Cameras
While it's important to understand potential security risks, here are methods that malicious actors might attempt to use and why they rarely work on properly secured iPhones.
1. Malicious Apps and Profiles

Malicious applications represent a significant security risk that attempts to gain unauthorized access to iPhone cameras. These deceptive programs exploit user trust to gain sensitive permissions.
While Apple's App Store security is robust, users should remain vigilant about permission requests and unusual behavior. The iOS permission system provides strong protection when users make informed decisions.
How This Method Works:
- Attackers create apps that request camera permissions
- The app may disguise its true functionality
- Once installed, it could potentially access the camera when running
Why This Usually Fails:
- iOS shows a camera indicator (green dot) whenever the camera is active
- Apps must request explicit permission to use the camera
- Apple's app review process screens for malicious functionality
- iOS prevents background camera access without user notification
Warning Signs:
- Apps requesting unnecessary permissions
- Battery draining unusually quickly
- The green camera indicator appears unexpectedly
- Strange files appearing in your photo library
2. Exploiting Software Vulnerabilities
Software vulnerabilities represent sophisticated attack vectors that attempt to bypass iOS security through programming flaws. These technical exploits target specific iOS versions with unpatched security issues.
The significant resources required for developing these exploits make them extremely rare and typically reserved for high-value targets. Regular iOS updates provide the strongest protection against these advanced threats.
How This Method Works:
- Finding unpatched security vulnerabilities in iOS
- Creating exploit code that bypasses security measures
- Delivering the exploit through websites, messages, or networks
- Gaining elevated privileges to access protected features
Why This Rarely Succeeds:
- Apple rapidly patches known vulnerabilities
- iOS has multiple security layers (sandboxing, permissions, etc.)
- Modern iPhones include hardware security features
- Exploits for current iOS versions are extremely rare and valuable
Protection Measures:
- Keep iOS updated to the latest version
- Only visit trusted websites
- Don't jailbreak your device
- Install iOS security updates immediately
Why Someone Might Want to Access an iPhone Camera Remotely
While accessing someone's iPhone camera without consent is illegal and a serious privacy violation, there are legitimate scenarios where camera monitoring may be necessary.
Here are some potential reasons, always considering the legal and ethical implications:
Parental Monitoring
Parents may need to monitor their children's phone activities for safety reasons. This might include ensuring they're not engaging in risky behaviors or communicating with potentially dangerous individuals.
It's crucial for parents to establish clear boundaries and communicate openly with their children about digital monitoring.
Business Security
Employers may need to secure company-owned devices to protect sensitive information. However, any monitoring should be:
- Transparent to employees
- Limited to business purposes
- Compliant with applicable laws
- Outlined clearly in company policies
Device Recovery
If an iPhone is lost or stolen, the owner might need remote access capabilities to recover personal data or locate the device.
Digital Wellbeing
Some individuals use monitoring as part of managing screen time and digital habits, either for themselves or family members.
How to Tell If Your iPhone Camera Is Being Hacked
Apple has implemented several security features to help you identify when your camera is in use:
1. Check for the Green Indicator Dot
Since iOS 14, Apple displays a green dot in the status bar whenever an app is using your camera. If you see this indicator when not using the camera yourself, it could be a sign of unauthorized access.
2. Review Camera Permissions
Go to Settings > Privacy > Camera to see which apps have permission to use your camera. Revoke access for any apps you don't recognize or don't need camera functionality.
3. Monitor Battery Usage
Unusual battery drain could indicate background processes accessing your camera. Check Settings > Battery to see which apps are consuming power.
4. Look for Unexpected Photos
Check your Photos app for images you don't remember taking, which could indicate someone has remotely triggered your camera.
5. Examine Network Activity
Unexpected increases in data usage might suggest something is transmitting camera data. Review your data usage in Settings > Cellular.
How to Protect Your iPhone Camera from Unauthorized Access
Securing your iPhone camera from potential intrusions is straightforward with these essential steps:
- Keep iOS Updated
- Use Strong Authentication
- Review App Permissions Regularly
- Be Cautious with Links and Attachments
- Consider a Camera Cover
- Avoid Jailbreaking
- Use Secure Wi-Fi Networks
Always install the latest iOS updates, which include security patches for known vulnerabilities. Enable automatic updates in Settings > General > Software Update.
Set up Face ID or Touch ID along with a complex passcode. Enable two-factor authentication for your Apple ID to prevent unauthorized access.
Periodically check which apps have camera access and revoke permissions for apps that don't need it or that you no longer use.
Don't click on suspicious links or download attachments from unknown sources, as these could contain exploits targeting your device.
For maximum peace of mind, you can use a physical camera cover when not using your front-facing camera.
Jailbreaking removes many of iOS's security protections, making your device more vulnerable to attacks.
Public Wi-Fi networks can be risky. Use a VPN when connecting to public networks to encrypt your data transmission.
FAQs on iPhone Camera Security
Many iPhone users have common questions about camera security and potential vulnerabilities. Here are answers to frequently asked questions about iPhone camera protection.
1. Can someone access my iPhone camera without me knowing?
On a non-jailbroken, updated iPhone, it's extremely difficult. Apple's security measures display a green indicator dot whenever your camera is active, and all apps must request explicit permission to use the camera.
2. Do iPhone camera covers damage the device?
Very thick camera covers might damage your screen when closed. Apple recommends using covers specifically designed for iPhones that are thin enough to not interfere with the device closing properly.
3. Can someone see me through my iPhone if it's off?
No, when an iPhone is completely powered off, the camera cannot be activated. However, if the phone is just in sleep mode (screen off), apps with camera permission could potentially access it.
4. Does resetting my iPhone remove spyware?
A factory reset will remove most types of malicious software from your iPhone. However, it's important to back up your important data first, then restore it cautiously to avoid reintroducing the same issues.
5. Can someone record you through your iPhone camera?
Yes, but it's very rare and usually requires spyware or jailbreaking.
6. Can hackers see you through your phone camera?
Possible, but highly unlikely on a non-jailbroken iPhone with Apple's security features.
Conclusion
Understanding how to hack into someone's iPhone camera could potentially be accessed remotely is the first step in protecting your privacy. While Apple's iOS provides robust security measures, keeping your device updated and being aware of unsafe tactics are essential practices.
If you need to monitor an iPhone camera for legitimate purposes, such as parental supervision or business security, always use transparent, legal solutions like SafeMyKid that respect privacy rights and operate with proper consent.



